Secure Shell (SSH), particularly its OpenSSH implementation, is a crucial tool for secure network communication. This guide will demonstrate how to install SSH on Linux Mint 21 or 20, offering a straightforward approach to enhancing your system’s security. SSH enables encrypted connections between computers, safeguarding data from unauthorized access or interception. This utility is widely adopted for remote server management and file transfers, making it an essential skill for system administrators and IT professionals.
Key Features of SSH (OpenSSH):
- Encrypted Communication: Ensures that all data transferred over the network is secure and protected from eavesdropping.
- Authentication Mechanisms: Supports various methods, including password and public key authentication, for verifying user identity.
- Port Forwarding: Allows secure tunneling of network connections, useful for bypassing firewalls and securely accessing remote services.
- Agent Forwarding: Facilitates secure connection chaining without exposing private keys.
- X11 Forwarding: Enables secure forwarding of X11 graphical applications over SSH sessions.
Mastering SSH installation on Linux Mint is a foundational step for anyone responsible for managing Linux systems. By following this guide, you’ll gain the knowledge to establish secure connections, ensuring your network communications remain confidential and tamper-proof.
Let’s dive into the process of installing SSH, starting with the requirements and followed by step-by-step instructions.
Install SSH on Linux Mint 21 or 20 via APT
Step 1: Refresh Linux Mint Packages Before SSH Installation
Begin by updating your Linux Mint system packages to ensure you have the latest versions. This step is crucial for maintaining system security and functionality.
In your terminal, execute:
sudo apt update && sudo apt upgradeThis command refreshes your system’s package index and upgrades all installed packages to their latest available versions.
Step 2: Install SSH (OpenSSH) via APT Command
Next, proceed to install OpenSSH, the secure networking utility. Type the following command in your terminal:
sudo apt install openssh-serverThis will download and install the OpenSSH server on your Linux Mint system. The service should start automatically upon completion, enabling secure remote access to your machine.
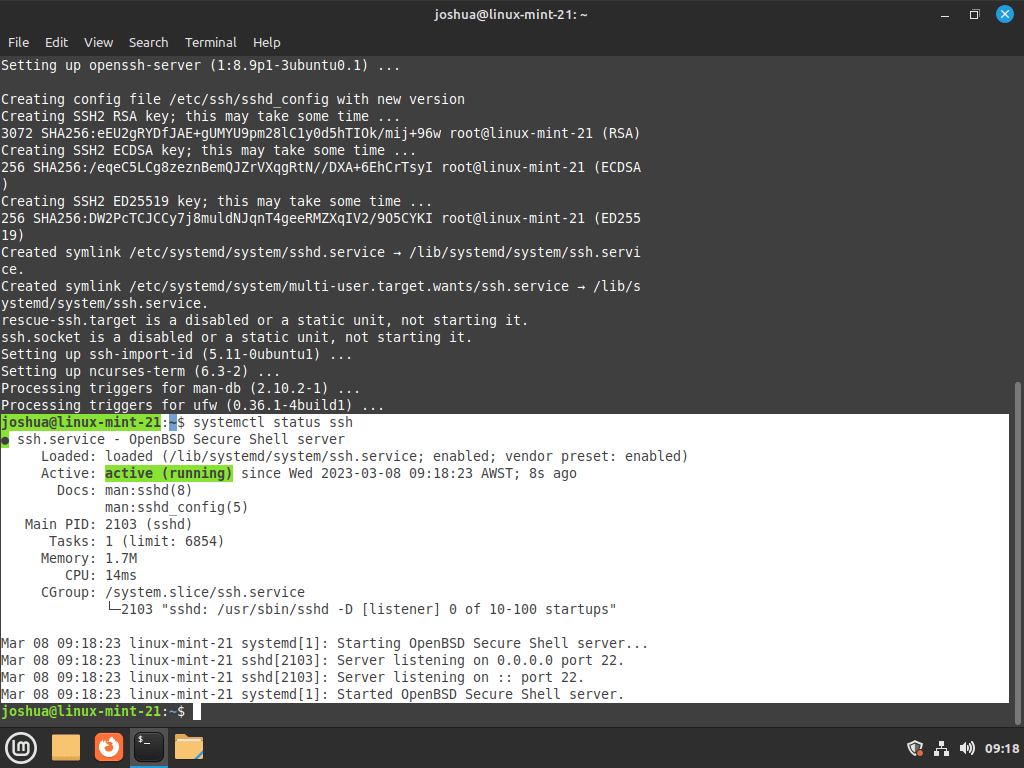
Step 3: Verify OpenSSH Installation on Linux Mint
To confirm the successful installation and active status of SSH, use this command:
systemctl status sshThis command checks the status of the SSH service. A successful output indicates that OpenSSH is correctly installed and operational.
Configure SSH on Linux Mint 21 or 20
Modifying OpenSSH Configuration for Enhanced Security
OpenSSH, by default, permits remote access to all users on your system. To bolster security, it’s advisable to restrict this access to specific users. You’ll need to edit the OpenSSH configuration file for these adjustments.
Open the file with a command-line text editor.
Here, we use nano:
sudo nano /etc/ssh/sshd_configRestricting Root Login
In the file, search for the line:
#PermitRootLogin prohibit-passwordUncomment this line and change it to:
PermitRootLogin noThis modification prevents the root user from logging in over SSH, a key step in securing your system.
Allowing Specific User Access
To limit SSH access to certain users, add:
AllowUsers your_usernameReplace your_username with the actual username. For multiple users, list them separated by spaces. This setting explicitly defines who can access your system via SSH.
Enforcing Public Key Authentication
For further security enhancement, consider disabling password-based authentication. Locate:
#PasswordAuthentication yesUncomment and modify it to:
PasswordAuthentication noThis change requires users to utilize public key authentication, a more secure method than traditional passwords.
Limiting Authentication Attempts
To mitigate brute-force attack risks, add a line to set a maximum number of authentication attempts:
MaxAuthTries 3This setting limits the number of failed login attempts, adding an extra layer of security against unauthorized access attempts.
After making these changes, save and exit the editor (in nano, this is done by pressing CTRL+X followed by Y).
Restarting SSH Service
To apply these configuration changes, restart the OpenSSH service:
sudo systemctl restart sshThis step ensures that all your modifications take effect immediately.
Basic SSH Commands with Linux Mint 21 or 20
Connecting to Your Machine Using SSH
With OpenSSH installed and configured on Linux Mint, you can initiate a secure remote connection to your machine. This is done using an SSH client from another computer.
Establishing an SSH Connection
To connect, launch the terminal on the client machine and enter:
ssh your_username@your_machine_ipReplace your_username with your desired username and your_machine_ip with your machine’s IP address.
Here, your_username is the username on the Linux Mint machine, and your_machine_ip is its IP address. This command initiates a secure SSH session to your Linux Mint system.
Commonly Used SSH Commands
Secure File Transfer (SCP)
To securely transfer files between your machine and the server, use the SCP command:
scp /path/to/local/file your_username@your_machine_ip:/remote/directory
This command copies a file from your local machine to the specified directory on the Linux Mint server.
Securely Copying Files from the Server
To copy files from the server to your local machine:
scp your_username@your_machine_ip:/path/to/remote/file /local/directory
This reverses the direction of the transfer, bringing files from the Linux Mint server to your local machine.
Running Commands Remotely
Execute a command on the Linux Mint server without logging into the interactive shell:
ssh your_username@your_machine_ip 'command'Replace 'command' with the command you wish to run remotely. It’s a quick way to check system status or perform simple tasks.
SSH Tunneling (Port Forwarding)
For secure port forwarding, use:
ssh -L local_port:localhost:remote_port your_username@your_machine_ip
This command creates a secure tunnel between the specified local and remote ports, useful for secure access to services running on the Linux Mint server.
Monitoring Active SSH Sessions
To view active SSH sessions on your Linux Mint server:
whoThis command lists all users currently logged in via SSH, providing a quick overview of active remote connections.
Exiting an SSH Session
To safely terminate your SSH session:
exitThis command closes the current SSH connection, ensuring a clean and secure logout from the Linux Mint server.
These basic SSH commands are essential for managing and interacting with your Linux Mint system remotely, offering both convenience and robust security.
Understanding SSH Fingerprints on Linux Mint 21 or 20
SSH fingerprints are integral to secure SSH communications, ensuring the authenticity of the server you’re connecting to. Below is an in-depth explanation of SSH fingerprints, including how they work and their importance in secure SSH connections.
What is an SSH Fingerprint?
An SSH fingerprint is a unique identifier for an SSH server, created as a hash of the server’s public key. This fingerprint is typically presented in formats like MD5 or SHA256. When you first connect to an SSH server, the SSH client displays this fingerprint and prompts you to verify it.
To view the SSH fingerprint of your server, use:
ssh-keygen -l -f /etc/ssh/ssh_host_rsa_key.pubWhy are SSH Fingerprints Important?
SSH fingerprints safeguard against man-in-the-middle attacks by ensuring you are connecting to the correct server. When a fingerprint is not recognized (i.e., not in your known hosts file), your SSH client alerts you, prompting a manual verification.
Upon first connection, you might see a message like:
The authenticity of host 'hostname (IP address)' can't be established.
RSA key fingerprint is SHA256:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.
Are you sure you want to continue connecting (yes/no/[fingerprint])?
Verifying SSH Fingerprints
Before accepting an unfamiliar fingerprint, cross-check it through a separate, secure channel – like internal documentation or direct confirmation from a system administrator.
After receiving the fingerprint through a secure channel, compare it with the one provided by your SSH client. If they match, you can safely proceed with the connection.
Managing SSH Fingerprints
Once a fingerprint is accepted, it’s stored in your known hosts file. Any future change in the server’s fingerprint triggers an alert from the SSH client, indicating a potential security risk.
To view fingerprints in your known hosts file:
cat ~/.ssh/known_hostsUnderstanding and managing SSH fingerprints is vital for ensuring secure remote connections, preventing unauthorized access, and maintaining the integrity of your SSH communications.
Configure UFW Firewall for SSH on Linux Mint 21 or 20
Configuring the Uncomplicated Firewall (UFW) for SSH on Linux Mint enhances your system’s security. UFW is a user-friendly interface for managing iptables firewall settings. This section covers how to install UFW, check its status, and secure SSH, especially if you’ve customized SSH ports.
Installing and Activating UFW
Before configuring firewall rules, ensure that UFW is installed and active on your system.
Step 1: Install UFW on Linux Mint
If UFW is not already installed, you can install it using the following command:
sudo apt install ufwStep 2: Enable UFW Service on Linux Mint for SSH
sudo ufw enableThis command starts the firewall, ensuring your rules are enforced.
Step 3: Check UFW Status
Confirm that UFW is running with the following:
sudo ufw status verboseThis displays the current status and rules of UFW.
Configuring UFW for SSH
Allowing SSH Connections
To ensure you can connect via SSH, allow the default SSH port (22):
sudo ufw allow sshOr, if you’re using a specific port for SSH:
sudo ufw allow 2222/tcpReplace 2222 with your custom SSH port number.
Limiting SSH Access
To restrict SSH access to a specific IP address:
sudo ufw allow from 192.168.1.100 to any port 22
Replace 192.168.1.100 with the IP address you wish to grant access.
Denying SSH on Other Ports
To prevent SSH connections on other ports:
sudo ufw deny 22If you’ve changed the SSH port, make sure to update this rule accordingly.
Important UFW Considerations with SSH
- Custom SSH Ports: If you’ve configured SSH to use a port other than the default (22), ensure your UFW rules reflect this change. Failure to do so can result in being locked out of your server.
- Multiple Rules: UFW allows the creation of multiple rules. Tailor these rules to your specific security needs, considering factors like network environment and the level of access required.
- Testing: After configuring UFW rules, test them to ensure they work as expected and that you have uninterrupted access to your server.
Configuring UFW for SSH on Linux Mint is a straightforward process that significantly improves your system’s security.
Conclusion
In this guide, we’ve covered essential steps to install, configure, and secure SSH on Linux Mint, ensuring robust and secure remote connections. We discussed updating packages, installing OpenSSH, and fine-tuning its configuration for enhanced security, including managing SSH fingerprints and setting UFW firewall rules. Always remember to verify SSH fingerprints for safe connections and tailor UFW rules to suit your security needs, especially if you’re using custom SSH ports.
By following these recommendations, you’ll maintain a secure, efficient remote access environment on your Linux Mint system, safeguarding it against unauthorized access while ensuring seamless operation.