The Metasploit Framework is a pivotal tool in cybersecurity, known for its robust penetration testing and vulnerability assessment capabilities. This guide is designed to navigate you through the process to install Metasploit Framework on Debian 12 Bookworm or the older stable releases of Debian 11 Bullseye or Debian 10 Buster. Utilizing the Metasploit Official APT for installation, it’s crucial to operate Metasploit in a dedicated system or a virtual environment to ensure the integrity of your primary tasks and sensitive applications.
Key Aspects of Metasploit Framework:
- Comprehensive Testing: Metasploit provides extensive options for penetration testing, helping identify vulnerabilities in systems and networks.
- Exploit Development: It aids in developing and testing exploits for identified vulnerabilities, enhancing system security.
- Payload Crafting: Users can create payloads to gain control over compromised systems, providing a deeper understanding of potential threats.
- Post-Exploitation Tools: Metasploit includes tools for extracting valuable data and maintaining access after a successful breach.
- Network Analysis: It offers capabilities to analyze network structures and identify potential entry points for securing the network.
Following this guide will give you practical insights into deploying the Metasploit CLI for various cybersecurity tasks, enhancing the security posture of your projects or services. As we delve deeper into the installation and utilization of Metasploit on Debian, you will be equipped to leverage this powerful tool to its fullest potential.
Install Metasploit Framework on Debian 12, 11, or 10 via APT
Step 1: Install Initial Required Packages For Metasploit on Debian
Before diving into the installation of Metasploit, ensuring that your Debian system is up-to-date and has all the necessary dependencies in place is essential.
Update and Upgrade Debian:
To keep your Debian system updated, execute the following commands:
sudo apt update
sudo apt upgradeInstall Required Dependencies:
With the system updated, proceed to install the dependencies essential for Metasploit:
sudo apt install curl ca-certificates apt-transport-https software-properties-common lsb-release postgresql -yStep 2: Import Metasploit APT Repository on Debian
Having the dependencies in place, the next step involves importing the Metasploit repository. This ensures you’re fetching genuine packages that haven’t been tampered with.
Import the GPG Key:
The GPG key ensures the authenticity of the packages. Import it with:
curl -fsSL https://apt.metasploit.com/metasploit-framework.gpg.key | sudo gpg --dearmor | sudo tee /usr/share/keyrings/metasploit.gpg > /dev/nullAdd the Metasploit Repository:
With the GPG key imported, proceed to add the Metasploit repository:
echo "deb [signed-by=/usr/share/keyrings/metasploit.gpg] https://apt.metasploit.com/ buster main" | sudo tee /etc/apt/sources.list.d/metasploit.list
Even though it says Buster, this is a generic repository now and will install the same package for all APT-based distros and does work on the latest Debian releases.
Step 3: Install Metasploit on Debian via APT Command
With the repository in place, it’s time to install the Metasploit Framework.
Refresh APT Cache:
Update your package list to ensure the latest version of Metasploit Framework is available:
sudo apt updateInstall Metasploit Framework:
Initiate the installation process with:
sudo apt install metasploit-frameworkFirst-Time Setup Process:
Upon successful installation, you’ll need to configure Metasploit for its first use:
msfconsole
During this setup, you might encounter several prompts:
- Setting up a New Database: It’s advisable to set up a new database for Metasploit. When prompted, type “yes” to proceed.
Would you like to use and setup a new database (recommended)?
- Initializing the Web Service: This step isn’t mandatory. By default, the answer is “no.” If you wish to enable the web service, type “yes.”
[?] Would you like to init the webservice? (Not Required) [no]:
- Final Configurations: After addressing the prompts, the system will finalize configurations. This might take a few minutes. You’ll be presented with information regarding the configuration process.
Upon completion, your Metasploit Framework is ready for use. As we delve deeper into subsequent sections, you’ll gain insights into harnessing the full potential of this powerful cybersecurity tool on your Debian system.
Metasploit Framework Terminal Commands on Debian 12, 11 or 10
Navigating the Metasploit Framework requires a good grasp of its terminal commands. This section provides a hands-on approach to using these commands effectively on Debian. A comprehensive table detailing all available commands will be presented by the end.
Step 1: Launching Metasploit Framework
To initiate the Metasploit Framework, access your terminal and input:
msfconsoleUpon execution, a banner will appear, displaying details about the current version, contributors, and some handy Metasploit Framework usage tips.
Step 2: Keeping Metasploit Updated
The Metasploit Framework is an evolving tool, regularly enhanced with new modules, features, and fixes. To ensure you’re using the latest version:
msfupdateThis command fetches and installs the most recent iteration of the Metasploit Framework.
Step 3: Searching for Exploits
A core functionality of the Metasploit Framework is its exploit search capability. To hunt for specific exploits:
search <search-term>Replace <search-term> with relevant keywords or terms. For instance, to find exploits associated with the Apache Struts vulnerability:
search strutsThis returns a list of exploits linked to the Apache Struts vulnerability.
Step 4: Engaging with Exploits
After pinpointing a desired exploit, you can activate its module:
use <exploit-name>Replace <exploit-name> with the exact exploit module name. If you’re aiming to utilize the Apache Struts exploit module:
use exploit/windows/http/struts2_rest_xstream
This action activates the exploit module, revealing details like its name, author, target platform, and associated payload.
Step 5: Configuring Exploit Parameters
Before deploying an exploit, adjusting specific parameters, such as target IP, port, or chosen payload, is often necessary. To view an exploit’s configurable options:
show optionsThis command lists all tweakable parameters for the active exploit module.
To modify a specific parameter:
set <option-name> <value>
For instance, to designate the RHOST parameter to a target system’s IP address:
set RHOST 192.168.1.100Step 6: Executing Exploits
With all parameters set, you can launch the exploit:
exploitIf the exploit succeeds, a confirmation message will appear, indicating a successful operation and the establishment of a session.
Leveraging Metasploit’s Meterpreter on Debian 12, 11 or 10
Meterpreter stands out as an advanced post-exploitation tool within the Metasploit Framework. It facilitates real-time interaction with compromised systems. To harness its capabilities, you first need an active session.
Step 1: Managing Sessions
To view all active sessions:
sessions -lThis command lists all sessions with their respective ID numbers.
To engage with a specific session:
sessions -i <session-id>For instance, to interact with the first session:
sessions -i 1This command initiates a Meterpreter shell for the chosen session, allowing you to run many commands on the compromised system.
Step 2: Extracting System Data
Upon securing a Meterpreter session, a logical first step is to collect data about the compromised system:
- System Overview:
sysinfoThis command provides a snapshot of the system, detailing the OS version, CPU type, and system architecture.
- User Identification:
getuidThis reveals the current user ID on the system.
- User Privileges:
getprivsThis enumerates the current user’s system privileges.
Step 3: File Transfers
Meterpreter facilitates file transfers between your machine and the compromised system:
- Uploading Files:
upload <local-file> <remote-file>For instance, to transfer a local file named data.txt to the compromised system’s C:\Temp directory:
upload /localpath/data.txt C:\Temp\data.txt- Downloading Files:
download <remote-file> <local-file>To retrieve a file named data.txt from the compromised system’s C:\Temp directory to your local machine:
download C:\Temp\data.txt /localpath/data.txtStep 4: Probing WordPress Vulnerabilities with Metasploit
Given WordPress’s ubiquity as a CMS, it’s often a target for potential threats. Using Metasploit, you can assess your WordPress installations for known vulnerabilities. Remember, exploiting systems without permission is both illegal and unethical.
To identify Metasploit modules related to WordPress vulnerabilities:
search wordpressThis command lists Metasploit modules tailored for WordPress vulnerabilities.
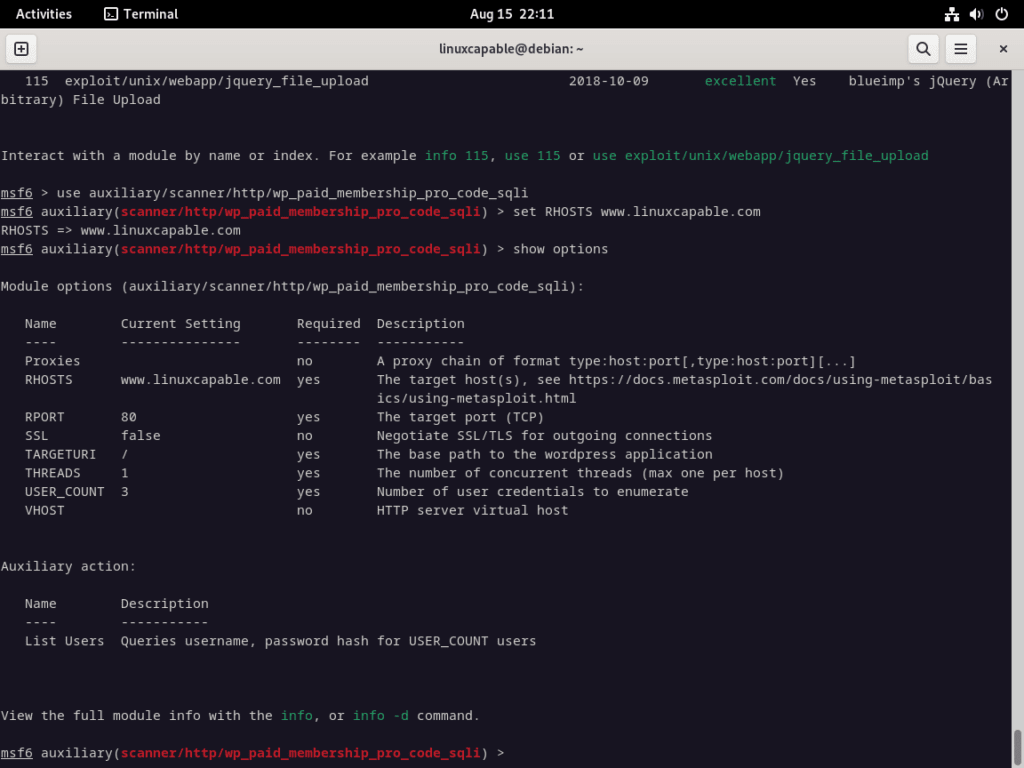
To engage with a specific module, for instance, the WP Paid Pro CODE SQLI vulnerability:
- Search for the Exploit: Once Metasploit is running, you can search for the exploit to ensure it’s available in your Metasploit version:
search wp_paid_membership_pro_code_sqli- Use the Exploit: If the exploit is available, you can load it using the
usecommand:
use auxiliary/scanner/http/wp_paid_membership_pro_code_sqli- Set the Options: You must set some options before running the exploit. At a minimum, you’ll need to set the RHOSTS option, which specifies the target IP address or domain:
set RHOSTS target_website_or_IPYou can view all the available options for the exploit by typing:
show optionsEnsure you configure any other necessary options based on your specific scenario.
- Run the Exploit: Once all the options are set, you can run the exploit:
runIf the target is vulnerable, Metasploit will attempt to exploit it and provide you with the results.
Metasploit Command Overview for Debian 12, 11 or 10
The Metasploit Framework is a vast tool with many commands at its disposal. While we’ve touched upon some commands in previous sections, it’s essential to understand those were just the tip of the iceberg. This section will provide a more detailed table of commonly used commands to help you navigate the framework more efficiently.
Exploit Commands
Exploit commands are pivotal in leveraging vulnerabilities within a target system.
| Command | Description |
|---|---|
search | Locate a specific exploit or payload. |
use | Choose an exploit or payload for deployment. |
show options | Display available options for the chosen exploit or payload. |
set | Define a value for a particular option. |
exploit | Launch the selected exploit. |
sessions | Oversee active Meterpreter sessions. |
back | Depart from the current exploit or payload context. |
Auxiliary Commands
Auxiliary commands cater to various tasks, from scanning and fuzzing to gathering crucial information.
| Command | Description |
|---|---|
search | Find a specific auxiliary module. |
use | Activate a desired auxiliary module. |
show options | Enumerate current options for the selected auxiliary module. |
set | Assign a value to a specific option. |
run | Initiate the chosen auxiliary module. |
back | Exit the current auxiliary module context. |
Post-Exploitation Commands
Once access to a system is secured, post-exploitation commands come into play, allowing various operations on the compromised system.
| Command | Description |
|---|---|
sysinfo | Retrieve detailed system data. |
getuid | Identify the active user ID. |
getprivs | Enumerate the privileges of the current user. |
shell | Access a system command shell. |
ps | List active processes. |
migrate | Transition to a different process. |
download | Retrieve a file from the compromised system. |
upload | Transfer a file to the compromised system. |
Database Commands
These commands facilitate interaction with the Metasploit Framework’s integrated database.
| Command | Description |
|---|---|
db_status | Verify the database’s operational status. |
db_rebuild_cache | Refresh the database cache. |
db_nmap | Incorporate an nmap scan result into the database. |
hosts | Enumerate all hosts registered in the database. |
services | List all services documented in the database. |
vulns | Detail all vulnerabilities recorded in the database. |
Module Management Commands
Managing modules within the Metasploit Framework is streamlined with these commands.
| Command | Description |
|---|---|
load | Integrate a module into the console. |
reload_all | Refresh all modules. |
unload | Remove a module from the console. |
info | Provide details about a specific module. |
edit | Modify a module’s parameters. |
Conclusion and Final Thoughts
In this comprehensive guide, we’ve installed the Metasploit Framework on various Debian versions, including Debian 12 Bookworm, Debian 11 Bullseye, and Debian 10 Buster. We’ve covered the foundational steps, delved into command overviews, and explored the potential of Metasploit’s Meterpreter. As with any powerful tool, using the Metasploit Framework with a clear understanding of its capabilities and implications is crucial.
Disclaimer: It’s imperative to emphasize that the Metasploit Framework, like any cybersecurity tool, should be used responsibly and ethically. Only deploy it for cybersecurity research on your platforms or entities granted explicit permission. Unauthorized or malicious use can lead to severe legal consequences and breaches of ethical standards.





Somthing is wrong. I can’t run msfconsole from user (only from root) after update metasploit. When I start msfconsole from user, I receive:
:~$ msfconsole
Verifying msfconsole data service
and the nothing happen anymore.
When I push Ctrl+C, I receive:
# terminated with exception (report_on_exception is true):
/opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:403:in `read’: stream closed in another thread (IOError)
from /opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:403:in `block (2 levels) in capture2e’
/opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:415:in `value’: Interrupt
from /opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:415:in `block in capture2e’
from /opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:227:in `popen_run’
from /opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:209:in `popen2e’
from /opt/metasploit-framework/embedded/lib/ruby/3.0.0/open3.rb:398:in `capture2e’
from /opt/metasploit-framework/embedded/framework/lib/msfdb_helpers/db_interface.rb:55:in `run_cmd’
from msfdb:660:in `run_msfconsole_command’
from msfdb:679:in `clear_default_data_service’
from msfdb:1061:in `’
How do I need remove metasploit-framework correctly? (After that I’ll tray install it again).
Hi Bill,
Which version of Debian are you installing metasploit on, so I can use the same version as yourself to check.
Thanks.
Debian 12 (bookworm).
This happened after entering a command “msfupdate” in the console.
Before that I could run msfconsole as a normal user. Now only from root.
Uninstalling and reinstalling the app didn’t help.
I uninstalled through the purge command. And I”ll tray install it again. May be this will help.
Seems to be working here, quickly installed it.
https://www.linuxcapable.com/cdn-cgi/image/width=1360,height=768,fit=crop,quality=50,format=auto,onerror=redirect,metadata=none/wp-content/uploads/2023/10/metasploit-working-on-debian-12.png
What I see i need to remove the msfupdate, its really not that important anymore and will cause confusion. since you can just use apt update now to update the installation given i’ve changed the method to link the apt.metasploit apt file directly to your sources list.
do all the other commands work? i tested quite a few, everything working well here.
Thank you for help.
I’m sorry. I didn’t answer few days. I reinstalled program. Now I can run it as a regular user. Only at the first start the program did not ask Setting up a New Database and Initializing the Web Service. There may be something left after the uninstalling (Although I deleted using the purge command).
Entering the show settings command gives the same result as you have.
“Search struts” is work too.
But, entering the “use exploit/windows/http/struts2_rest_xstream” gives result:
msf6 > use exploit/windows/http/struts2_rest_xstream
[-] No results from search
[-] Failed to load module: exploit/windows/http/struts2_rest_xstream
msf6 >
ZSH: sudo nala install metasploit-framework
=========================================================================================
Installing
=========================================================================================
Package: Version: Size:
metasploit-framework 6.3.40+20231021102610~1rapi 327.1 MB
d7-1
=========================================================================================
Summary
=========================================================================================
Install 1 Packages
Total download size 327.1 MB
Disk space required 810.6 MB
Do you want to continue? [Y/n] y
Error: Client error ‘404 Not Found’ for url
‘http://downloads.metasploit.com/data/releases/metasploit-framework/apt/pool/main/m/metas
ploit-framework/metasploit-framework_6.3.40%2B20231021102610%7E1rapid7-1_amd64.deb’
For more information check: https://httpstatuses.com/404
╭─ Downloading… ────────────────────────────────────────────────────────────────────────╮
│ Total Packages: 0/1 │
│ Starting Downloads… │
│ Time Remaining: -:–:– ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 0.0% • 0.0/327.1 MB • ? │
╰───────────────────────────────────────────────────────────────────────────────────────╯
Error: Download failure. The following downloads failed:
metasploit-framework_6.3.40+20231021102610~1rapid7-1_amd64.deb
Thank you for bringing this to my attention. I’ve checked from my side as well and encountered the same 404 error. It seems every version and architecture is currently returning a 404. I’m inclined to believe that the issue might be on Metasploit’s end. I’ve been utilizing this method for many years and this is the first time I’ve come across such a widespread 404 issue. I’ll run another test tomorrow.
I think you need to change this repository address:
http://downloads.metasploit.com/data/releases/metasploit-framework/apt buster main”
Now it is not correct line. They changed the package address from http://downloads.metasploit.com to https://apt.metasploit.com/
But I don’t know how change it correct.
I think you know
Thanks for that link, they have changed the urls. I re-installed it on Debian 12 with new link, and works.
Ok, so if you imported the old list just remove it with the following command:
sudo rm /etc/apt/sources.list.d/metasploit.list
then do:
echo “deb [signed-by=/usr/share/keyrings/metasploit.gpg] https://apt.metasploit.com/ buster main” | sudo tee /etc/apt/sources.list.d/metasploit.list
The GPG key should still work, as I said it worked fine here with the new repository link above, let me know if you have any issues.
Thanks for the comment.