For those prioritizing security while working with Debian-based systems, learning to install Chkrootkit on Debian 12 Bookworm, Debian 11 Bullseye, or Debian 10 Buster is crucial. Chkrootkit is a lightweight, open-source tool designed for detecting rootkits, which are stealthy and malicious software tools often used by attackers to gain unauthorized access to systems.
Key Features of Chkrootkit:
- Lightweight and Portable: With its minimalistic design, Chkrootkit occupies little disk space and efficiently uses system resources.
- Command-Line Based: The tool operates via the command line, offering users complete control, and the ability to automate tasks through scripting.
- Versatile Detection Methods: Chkrootkit utilizes various techniques, including signature analysis and behavior monitoring, to identify and flag potential rootkits effectively.
- Open Source: Being open-source, Chkrootkit invites community collaboration, resulting in a tool that is not only more secure but also consistently improved and updated.
- Cross-Platform Support: Although this guide focuses on Debian, Chkrootkit is compatible with various UNIX systems.
- Regular Updates: Active maintenance of Chkrootkit ensures it can detect the latest rootkits and remains a reliable tool for system administrators and security professionals.
Understanding the installation and functionality of Chkrootkit is a fundamental step in enhancing the security of your Debian systems, whether you’re working with Debian 12 Bookworm, Debian 11 Bullseye, or Debian 10 Buster. This guide aims to equip you with the knowledge to install and effectively utilize Chkrootkit, thereby enabling you to safeguard your systems against rootkits and similar security threats proactively.
Install Chkrootkit on Debian 12, 11, or 10 via APT
Step 1: Check For Updates Before Chkrootkit Installation
First, refresh the package lists on your Debian Linux system to install Chkrootkit. Refreshing the package lists provides your system with up-to-date information on available packages and their versions while priming it with the latest security patches and software updates. Execute the following command in the terminal to accomplish this:
sudo apt update && sudo apt upgradeThis command retrieves the most recent package information from the repositories and upgrades any installed packages to the latest versions if available.
Step 2: Install Chkrootkit on Debian 12, 11, or 10 via APT Command
After updating your system, proceed with the installation of Chkrootkit. The APT package manager, the default software management system for Debian, facilitates a streamlined software installation process. Execute the following command to use APT for installing Chkrootkit:
sudo apt install chkrootkitExecuting this command initiates the installation of the Chkrootkit package.
Step 3: Confirm Chkrootkit Installation on Debian via APT
After installing Chkrootkit, confirm a successful installation and proper setup for immediate use. This confirmation ensures the process’s integrity and prepares you for effective Chkrootkit utilization. Validate the installation by entering the Chkrootkit version command in the terminal:
chkrootkit -VThis command will display the version of Chkrootkit installed, affirming that the software is in place and operational.
Install Chkrootkit on Debian 12, 11, or 10 via source
Step 1: Download Chkrootkit Source on Debian
First, you need to download the source code of Chkrootkit from its official website. Doing so guarantees that you are obtaining the latest software version, which might include new features or security enhancements. In the terminal, navigate to the directory where you intend to store the source code. Then, execute the command below to download the Chkrootkit source code archive:
wget ftp://chkrootkit.org/pub/seg/pac/chkrootkit.tar.gzThis command fetches the Chkrootkit source code in a compressed archive format, storing it in your specified directory.
Step 2: Extract Chkrootkit Source Archive on Debian
After downloading the archive, extracting the source code is next. This step is indispensable as it enables you to access the files and directories necessary for the compilation and installation.
To extract the source code, execute the following command:
tar -xvzf chkrootkit.tar.gzStep 3: Configure and Build Chkrootkit on Debian
Before compiling Chkrootkit, ensuring that your Debian Linux system has the requisite packages is essential. These include the GNU Compiler Collection (GCC) and the make utility, which is indispensable for the compilation process.
To install them, use the following command:
sudo apt install gcc make build-essentialPlease note that the correct package name is build-essential and not build-essentials.
Now, navigate to the directory containing the extracted Chkrootkit source code. Use the cd command as shown below, but make sure to replace {your-version-number} with the actual version number of the downloaded Chkrootkit source code:
cd chkrootkit-{your-version-number}
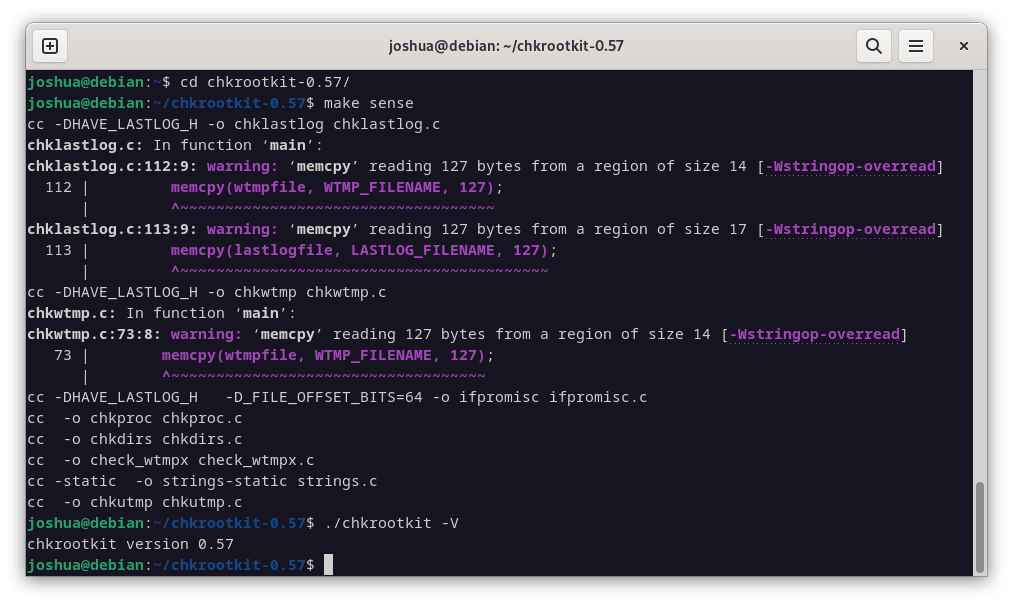
make senseThis command compiles the Chkrootkit source code, generating an executable binary file.
Step 4: Confirm Chkrootkit Installation on Debian
After compiling and setting up Chkrootkit, judiciously validate the installation process’s successful completion. This confirmation ensures Chkrootkit’s preparedness and readiness for utilization. Execute the Chkrootkit version command below to do this:
./chkrootkit -VThis command shows the installed Chkrootkit version, verifying the software’s correct installation and operation.
Step 5: Move Chkrootkit for System Global Access on Debian
After successfully compiling Chkrootkit, it is advisable to move the Chkrootkit directory to a more standard location within the file system and make the executable accessible system-wide. A common practice is to place such software in /usr/local/bin for global accessibility.
Start by moving the Chkrootkit directory to /usr/local/share. First, ensure that you are in the parent directory of the Chkrootkit directory (one level above chkrootkit-{your-version-number}). Then, execute the following command:
sudo mv chkrootkit-{your-version-number} /usr/local/share/chkrootkitNext, create a symbolic link to the Chkrootkit executable in /usr/local/bin. This makes Chkrootkit accessible anywhere in the system without navigating to its directory. Execute the following command to create the symbolic link:
sudo ln -s /usr/local/share/chkrootkit/chkrootkit /usr/local/bin/chkrootkitNow, Chkrootkit is globally accessible. You can verify this by simply running the Chkrootkit version command from anywhere in the terminal:
chkrootkit -VThis additional step streamlines the utilization of Chkrootkit, making it easily accessible and aligning with standard practices for managing software installations on Linux systems.
Basic Commands with Chkrootkit for Rootkit Detection on Debian 12, 11 or 10
Before diving into the steps, it’s crucial to note that when utilizing Chkrootkit for scanning your system, you will typically need to execute it with sudo. This is because Chkrootkit requires elevated privileges to thoroughly inspect all areas of your Debian Linux system, including those not accessible by unprivileged users. Running Chkrootkit with sudo ensures that it can effectively scan for rootkits across the entire system.
Now, let’s proceed to utilizing and scanning with Chkrootkit.
Step 1: Initiate Rootkit Scanning Using Chkrootkit on Debian
With Chkrootkit installed, it’s time to utilize its features to safeguard your Debian Linux system. A primary feature of Chkrootkit is to scan your system for any rootkits. Rootkits are malicious software that can give unauthorized access and control over your system. In a terminal, use this command to perform a thorough scan:
sudo chkrootkitThis command initiates a detailed scan, scrutinizing various elements of the system for irregularities that might indicate the presence of rootkits.
In case you desire a more streamlined output that only flags potential issues without overwhelming you with details, make use of the quiet mode:
sudo chkrootkit -qThis limits the output, making it easier to spot any red flags.
Step 2: Establish an Automatic Scanning Regimen with Chkrootkit
Maintaining a secure environment requires continuous vigilance. Configure Chkrootkit to perform daily scans automatically by tweaking its configuration file.
Open the configuration file using this command:
sudo nano /etc/chkrootkit/chkrootkit.confIn this file, search for the RUN_DAILY attribute and make sure its value is set to TRUE. This typically is the default setting, but confirming ensures that automated daily scans are active.
RUN_DAILY="true"
After editing, save the file by pressing CTRL + O and exit the editor by pressing CTRL + X.
If you installed Chkrootkit from source, as opposed to installing it from the Debian repositories, it does not come with a default configuration file like chkrootkit.conf. The chkrootkit.conf file is generally part of the packaged version of Chkrootkit that comes with Debian repositories.
When manually installing Chkrootkit from the source, you can run the tool directly without a configuration file. However, if you want to automate or configure the scans, you must create your script or cron job.
For example, if you want to create a daily cron job to run Chkrootkit, you could create a simple shell script to run the desired chkrootkit command, and then schedule this script using cron.
Here’s an example of how you can do it:
Create a script file, e.g., daily_chkrootkit.sh:
#!/bin/bash
/usr/local/bin/chkrootkitMake the script executable:
chmod +x daily_chkrootkit.shEdit the crontab file to schedule the script to run daily:
sudo crontab -eAdd the following line to the crontab file to run the script daily at a specific time (e.g., 2:00 AM):
0 2 * * * /path/to/daily_chkrootkit.shThis way, you can effectively automate Chkrootkit scans even when installing from source.
Step 3: Delve into Chkrootkit’s Array of Commands and Documentation
For a tool as potent as Chkrootkit, understanding its capabilities is crucial. Chkrootkit comes with various commands and options tailored to specific scanning needs.
Access the Help menu to get an overview of commands by executing:
chkrootkit -hThis provides a quick reference guide to Chkrootkit’s options and functionalities.
For an in-depth understanding, consider studying Chkrootkit’s manual page, accessible through:
man chkrootkitThis opens a wealth of information, explaining commands, options, and use cases for Chkrootkit.
Step 4: Experimenting with Advanced Scanning Options
Chkrootkit offers specialized options for customized, enhanced scanning. You can check for a specific rootkit by specifying its name:
sudo chkrootkit wormscanThis command scans for worms.
Another advanced command lets you check for the last modification date of the network service binaries:
sudo chkrootkit -l /sbinThis example command inspects the /sbin directory for any modifications.
Using Chkrootkit effectively requires learning and experimenting with its various options to align the scans with your security objectives. Customizing the depth and focus of your scans allows for more robust and focused protection.
Conclusion
This article guides you through installing and configuring Chkrootkit on Debian Linux (versions 12/11/10), from source code extraction to compilation and installation. We covered its practical use for scanning and protecting your system against rootkits, emphasizing the importance of establishing automated scans and learning advanced options to enhance security. Remember, while using Chkrootkit is crucial, maintaining security requires ongoing effort, including regular software updates and staying informed on best security practices.