Fail2ban, a powerful security tool, significantly enhances server protection by monitoring and blocking unauthorized access attempts. This guide will demonstrate how to install Fail2ban with Firewalld on Fedora Linux, a combination that fortifies your server’s defenses. Integrating Fail2ban with Firewalld lets you leverage a dynamic duo to secure your system against brute-force attacks and unauthorized intrusions.
Key Features of Fail2ban with Firewalld:
- Automated Blocking: Quickly bans IP addresses that exhibit suspicious behavior, reducing the risk of cyber attacks.
- Log Analysis: Scans server logs for patterns indicating unauthorized access attempts.
- Customizable Rules and Filters: Tailor the security settings to meet your server’s specific needs.
- Email Notifications: Sends alerts to keep you informed of potential security breaches.
- Extensive Service Support: Compatible with various services like SSH, FTP, and HTTP, providing comprehensive security coverage.
Incorporating Fail2ban with Firewalld into your Fedora Linux setup provides a robust security layer. The subsequent sections detail the steps to integrate these tools, ensuring your server is safeguarded against a broad spectrum of digital threats.
Install Firewalld on Fedora Linux via DNF
Step 1: Refresh Fedora Linux System Packages
Begin by updating your system’s package list. This is a crucial step to ensure compatibility and avoid conflicts during installation. Open your terminal and input the command:
sudo dnf upgrade --refreshThis command refreshes and updates all your system packages. It’s advisable to reboot your system if the update includes significant changes, such as a kernel upgrade, to ensure all updates are correctly applied.
Step 2: Install Firewalld via DNF Command
Next, install Firewalld, a dynamic firewall manager on Fedora Linux. With your system now up-to-date, execute the following command to install Firewalld:
sudo dnf install firewalldFirewalld manages network traffic through customizable rules and is a critical component for system security.
Step 3: Enable and Start Firewalld
Once installed, it’s essential to set Firewalld to start automatically at system boot and launch it immediately. Use this command to enable and start Firewalld:
sudo systemctl enable firewalld --nowThis command ensures Firewalld is active and running after the system restarts, maintaining continuous network protection.
Step 4: Check Firewalld Status
Verifying the operational status of Firewalld is essential to confirm it’s running correctly. Use the following command to check its status:
sudo firewall-cmd --stateA successful output indicates Firewalld is active and functioning as expected.
Step 5: List Existing Firewalld Rules
Before integrating Fail2Ban, it’s crucial to understand the current rules set in Firewalld. Familiarize yourself with these rules by listing them out:
sudo firewall-cmd --list-allUnderstanding the current Firewalld rules is critical to setting up Fail2Ban correctly, as this ensures it integrates smoothly with your existing security measures, avoiding potential conflicts. With Firewalld now operational on your Fedora system, we can proceed with installing Fail2Ban.
Install Fail2ban on Fedora Linux via DNF
Step 1: Install Fail2Ban and its Firewalld Integration
With Firewalld already set up on your system, you can install Fail2Ban, a critical tool for server security. Fail2Ban is readily available in the Fedora repository, ensuring you get the latest and most secure version. To install Fail2Ban along with its Firewalld integration, use the command:
sudo dnf install fail2ban fail2ban-firewalldThis command installs both Fail2Ban and the necessary components to work seamlessly with Firewalld.
Step 2: Check Fail2Ban Version
After installing, it’s essential to verify that Fail2Ban is correctly installed. Check the version of Fail2Ban to confirm this:
fail2ban-client --versionThis step assures you that the installed version is up to date.
Step 3: Enable and Start the Fail2Ban Service
Next, activate Fail2Ban to start automatically on system boot and to begin functioning immediately. Execute this command:
sudo systemctl enable fail2ban --nowEnabling Fail2Ban ensures continuous monitoring and protection against unauthorized access attempts.
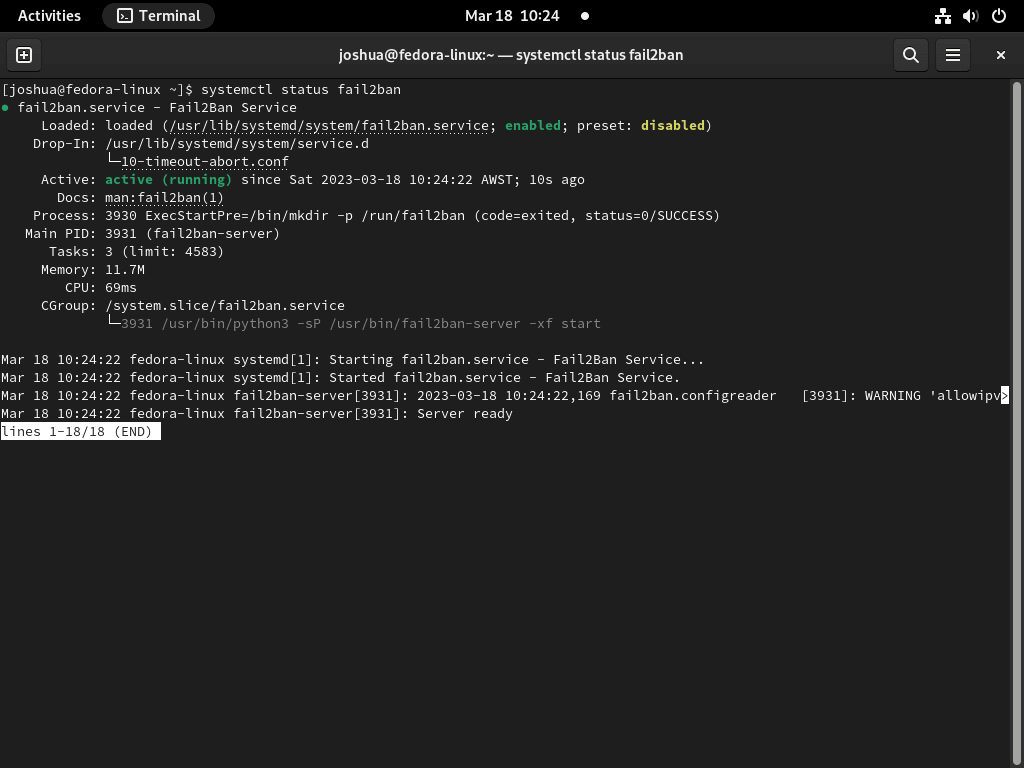
Step 4: Check the Fail2Ban Service Status
To ensure that Fail2Ban is operational, check its service status:
systemctl status fail2banA successful output indicates that Fail2Ban monitors your server for suspicious activities.
Create a Fail2ban Configuration File on Fedora Linux
Step 1: Create a Custom Configuration File
After installing Fail2Ban, it’s important to configure it to suit your specific needs. Fail2Ban primarily utilizes two configuration files: /etc/fail2ban/jail.conf and /etc/fail2ban/jail.d/00-firewalld.conf. To safeguard your custom configurations against overwrites during updates, you should create a .local extension copy of the configuration file.
First, replicate the jail.conf file to create a jail.local file. This is done using the cp (copy) command:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.localThis step ensures you have a separate configuration file that won’t be automatically replaced during software updates.
Next, open the jail.local file in a text editor, such as Nano, for modification:
sudo nano /etc/fail2ban/jail.localWithin this file, locate the section with IPTABLES settings. These should be replaced with Firewalld-specific configurations, reflecting the change in the firewall backend:
; Replace this
banaction = iptables-multiport
banaction_allports = iptables-allports
; With this
banaction = firewallcmd-rich-rules[actiontype=]
banaction_allports = firewallcmd-rich-rules[actiontype=]
Step 2: Customize Fail2Ban Settings
Configuring Fail2Ban to meet your security requirements is crucial. This involves setting parameters like ban time, whitelisting IPs, and email notifications.
Ban Time Increment:
To escalate the ban duration for repeat offenders, adjust the bantime.multipliers setting. By uncommenting and modifying this line, you can define how the ban time increases with each subsequent offense:
bantime.multipliers = 1 5 30 60 300 720 1440 2880This configuration means that the initial ban time is 1 minute, increasing to 5 minutes, then 30 minutes, and so on, up to a maximum of 48 hours.
Whitelist IPs
Excluding specific IPs from bans is sometimes necessary, especially for trusted networks or your IP. This is where the ignoreip setting comes into play. Modify it to add any IP addresses you wish to whitelist:
ignoreip = 127.0.0.1/8 ::1 180.53.31.33Default Ban Time Settings
You can set general ban time rules for various services. For instance, adjusting the ban time and retry limits for the Apache service:
[apache-noscript]
enabled = true
port = http,https
logpath = %(apache_error_log)s
bantime = 1d
maxretry = 3In this example, the ban time is set to 1 day with a maximum retry limit of 3 attempts.
Email Notifications
Configure Fail2Ban to send email notifications in case of a ban action. This is done by setting the destemail and sender fields:
destemail = admin@example.com
sender = fail2ban@example.comThis configuration ensures you are promptly informed of any security actions taken by Fail2Ban.
Additional Fail2ban Jails Configuration on Fedora Linux
Nginx Jail
A custom jail can be created for Nginx servers to block requests with invalid hostnames. This is useful for mitigating attacks that target non-existent domains on your server:
[nginx-badhost]
enabled = true
port = http,https
logpath = /var/log/nginx/error.log
maxretry = 3
bantime = 2hPostfix Jail
To protect your Postfix mail server from spam-related breaches, create a jail specifically targeting spam activities:
[postfix-spam]
enabled = true
port = smtp,ssmtp
logpath = /var/log/mail.log
maxretry = 5
bantime = 1hDovecot Jail
For Dovecot IMAP services, it’s essential to have a jail that targets unauthorized access attempts, enhancing the security of your email server:
[dovecot-auth]
enabled = true
port = imap,imaps
logpath = /var/log/dovecot.log
maxretry = 5
bantime = 1hRestart Fail2Ban
After all configurations are set, restart Fail2Ban to activate the changes. This ensures that your newly set parameters are applied, and the system is protected according to the new rules:
sudo systemctl restart fail2banCustom Filters and Actions with Fail2ban on Fedora Linux
Creating custom filters and actions in Fail2Ban empowers you to tailor your server’s security to meet specific needs on Fedora Linux.
Custom Filters
Fail2Ban utilizes filters, defined by regular expressions, to identify unauthorized access attempts in log files. These filters are located in the /etc/fail2ban/filter.d directory.
Creating a Custom Filter
To create a custom filter, you open a new file in the filter directory.
Execute the command:
sudo nano /etc/fail2ban/filter.d/mycustomfilter.confThis step involves using nano, a text editor, to create and open a new filter configuration file.
Next, define your custom filter within this file. The filter definition usually comprises a failregex, a regular expression that matches log entries indicating unauthorized access attempts. For instance:
[Definition]
failregex = ^.*unauthorized access attempt from <HOST>.*$
ignoreregex =In this example, the failregex pattern is set to match any log entry that includes an unauthorized access attempt from a specific IP address, denoted by <HOST>.
Custom Actions
In Fail2Ban, actions define how the system responds to detected offenses and are stored in the /etc/fail2ban/action.d directory.
Creating a Custom Action
To create a custom action, start by creating a new file in the action directory:
sudo nano /etc/fail2ban/action.d/mycustomaction.confThis opens a new file in nano for editing your custom action’s configuration.
Now, in this file, add your action definition:
[Definition]
actionstart = /usr/local/bin/mycustomaction start <name>
actionstop = /usr/local/bin/mycustomaction stop <name>
actioncheck = /usr/local/bin/mycustomaction status <name>
actionban = /usr/local/bin/mycustomaction ban <ip>
actionunban = /usr/local/bin/mycustomaction unban <ip>Replace /usr/local/bin/mycustomaction with the path to your custom action script. Parameters like <name> and <ip> will be dynamically replaced by Fail2Ban when the action is executed.
Integrating Custom Filters and Actions
After creating your custom filters and actions, integrate them into your jail configuration. For example:
[mycustomjail]
enabled = true
port = 8080
logpath = /var/log/mycustomservice.log
filter = mycustomfilter
action = mycustomaction
maxretry = 3
bantime = 1hThis jail configuration employs the custom filter and action you created, monitoring the specified log file and enforcing bans based on your settings.
Restarting Fail2Ban
To activate your new configurations, restart Fail2Ban:
sudo systemctl restart fail2banThis ensures all your custom settings are loaded and operational.
Fail2ban-Client for Ban and Unban Operations on Fedora Linux
The fail2ban-client command is integral for managing Fail2Ban configurations and jails, particularly for manual ban and unban operations on IP addresses.
Ban an IP Address
To ban an IP address in a specific jail, execute the command:
sudo fail2ban-client set <jail-name> banip <ip-addresss>In this command, replace <jail-name> with the relevant jail name and <ip-address> with the IP you wish to ban. For example:
sudo fail2ban-client set apache-badbots banip 192.168.1.1This particular command will ban the IP address 192.168.1.1 in the apache-badbots jail, effectively preventing access from that IP to the services protected by this jail.
Unban an IP Address
To reverse a ban, unbanning an IP address in a specific jail, use:
sudo fail2ban-client set <jail-name> unbanip <ip-address>Here, substitute <jail-name> and <ip-address> with the appropriate jail name and IP address. For instance:
sudo fail2ban-client set apache-badbots unbanip 192.168.1.1This command will lift the ban on the IP address 192.168.1.1 from the apache-badbots jail.
Display the List of Banned IP Addresses
To view a list of currently banned IP addresses in a specific jail, the command is:
sudo fail2ban-client status <jail-name>Replace <jail-name> with the name of the jail you wish to inspect.
For example:
sudo fail2ban-client status apache-badbotsExecuting this command will show the status of the apache-badbots jail, including a list of all IP addresses currently banned by that jail.
Help and Documentation
For further assistance or details about the fail2ban-client command, utilize the -h flag:
sudo fail2ban-client -hThis command will display a help menu, offering a comprehensive list of available options and commands for the fail2ban-client.
Utilizing the fail2ban-client command streamlines the process of managing jails, and enables the manual banning and unbanning of IP addresses, along with the ability to monitor the status of your Fail2Ban configurations.
Verifying Firewalld and Fail2ban Integration on Fedora Linux
Ensuring that Firewalld and Fail2ban function together correctly is crucial for optimal server security. A straightforward test can confirm their integration.
Enabling the SSHD Jail for Testing
To test the integration between Fail2ban and Firewalld, temporarily enable the SSHD jail in Fail2ban, even if it’s not in use. This action allows for a practical assessment of the system’s functionality.
Open the Fail2ban jail configuration file using this command:
sudo nano /etc/fail2ban/jail.localThis command opens the Fail2ban configuration file in the nano editor, allowing you to modify the settings.
In the file, locate the [sshd] section and change the enabled setting to true:
[sshd]
enabled = trueSetting this to true activates the SSHD jail, a crucial step for testing.
After modifying the file, save the changes and exit the editor. Then, restart Fail2ban to apply these changes:
sudo systemctl restart fail2banRestarting Fail2ban ensures that the new configuration is active.
Testing the Ban Functionality
To manually test the ban functionality:
Ban an IP address in the SSHD jail using the fail2ban-client command:
sudo fail2ban-client set sshd banip 192.155.1.7This command instructs Fail2ban to ban the specified IP address in the SSHD jail.
Next, verify if Firewalld has applied the ban. Use the firewall-cmd command to list the rich rules:
firewall-cmd --list-rich-rulesThis lists all rich rules in Firewalld, including those added by Fail2ban.
An example output indicating successful integration:
rule family="ipv4" source address="192.155.1.7" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"Fail2ban and Firewalld have correctly banned this IP address, as the output indicates.
Reverting the Changes
After completing the test, revert the changes if you no longer require the SSHD jail:
Open the Fail2ban jail configuration file again:
sudo nano /etc/fail2ban/jail.localFind the [sshd] section and reset the enabled setting back to false:
[sshd]
enabled = falseSave your changes and exit the editor. Finally, restart Fail2ban to apply the reversal:
sudo systemctl restart fail2banRestarting Fail2ban deactivates the SSHD jail, returning the configuration to its original state.
Monitor Fail2Ban Logs on Fedora Linux
Effectively monitoring Fail2Ban logs is essential to ensure the smooth operation of your jails on Fedora Linux. The default location for Fail2Ban logs is /var/log/fail2ban.log.
Watching the Log File in Real-Time
To observe the log file as events occur, utilize the tail -f command. This allows you to view log entries in real time, which is particularly useful for immediate troubleshooting or monitoring ongoing activities:
tail -f /var/log/fail2ban.logExecuting this command in a terminal window maintains the log file open and updates it in real-time with each new entry added.
Displaying a Specific Number of Lines from the Log File
If you need to review a specific number of recent log entries, the tail command can be modified with the -n flag. This flag specifies the number of lines from the end of the file to display:
tail -f /var/log/fail2ban.log -n 30This example will display the last 30 lines of the log file. You can replace 30 with any number of lines that fit your requirements.
Searching the Log File for Specific Keywords or IP Addresses
For more targeted log analysis, such as finding entries related to a specific IP address or event, use the grep command. This tool searches through the log file for specified patterns:
grep '192.168.1.1' /var/log/fail2ban.logIn this example, grep is used to locate all occurrences of the IP address 192.168.1.1 in the Fail2Ban log. This method is particularly effective for quickly identifying actions taken against a specific IP or identifying patterns related to certain types of security incidents.
Managing Fail2ban on Fedora Linux
Remove (Uninstall) Fail2ban From Fedora
When you no longer need Fail2Ban on your Fedora system, uninstall it to remove the software and its related unused dependencies. This action ensures your system remains tidy and efficient.
Execute the following command to uninstall Fail2Ban and its Firewalld integration:
sudo dnf remove fail2ban fail2ban-firewalldNote that this will also remove all the unused dependencies installed with Fail2Ban.
Conclusion
Congratulations on successfully installing and configuring Fail2Ban with Firewalld on your Fedora Linux system! You’ve taken a significant step towards enhancing your server’s security, shielding it effectively from brute-force attacks and unauthorized intrusions. Remember, regular monitoring and updates are vital to maintaining robust security. Stay vigilant, keep your system up-to-date, and your server will remain a tough nut to crack for potential threats.