In network security, firewalls are pivotal in safeguarding systems from potential threats. While Linux systems traditionally employ iptables for this purpose, their intricate configuration can be challenging for many. For Debian users, there’s a more intuitive solution at hand. This guide will demonstrate how to install UFW Firewall on Debian 12 Bookworm, Debian 11 Bullseye, or Debian 10 Buster, offering a streamlined approach to bolstering system security.
Advantages of Using UFW Over Iptables:
- Intuitive Syntax: UFW, short for Uncomplicated Firewall, boasts a user-friendly syntax. This simplicity allows users to effortlessly define rules, such as “ufw allow ssh” or “ufw deny http”, eliminating the need for intricate iptables commands.
- Pre-configured Defaults: UFW comes equipped with default settings that strike a balance between security and functionality. Essential services like SSH and DNS operate unhindered, reducing potential misconfigurations.
- Efficient Logging: With its integrated logging capabilities, UFW enables users to keep a vigilant eye on network traffic, aiding in identifying potential security anomalies.
- Seamless Debian Integration: As Debian’s default firewall solution, UFW seamlessly integrates with the system’s components. This integration facilitates easy installation and management via Debian’s package management tools.
- Iptables Compatibility: Operating with iptables as its backbone, UFW ensures full compatibility with iptables rules, allowing users acquainted with iptables to transition their rules to UFW without losing functionality.
With these benefits in mind, let’s delve into the installation and configuration process of the UFW Firewall on your Debian system.
Install UFW on Debian 12, 11 or 10
If you’re new to Debian Linux and the command terminal, learning to secure your system with a firewall can be daunting. Fortunately, Debian users can easily use Uncomplicated Firewall (UFW) to manage their system’s security.
Before installing UFW, it’s essential to ensure that your system is up-to-date to avoid any conflicts during installation. Run the following command to update your system:
sudo apt update && sudo apt upgradeNote that if your Linux Kernel was updated, you may need to reboot your system.
Once your system is updated, you can install UFW by running the following command:
sudo apt install ufwUnlike other Debian-based distributions like Ubuntu, UFW isn’t installed by default in Debian. Therefore, it’s crucial to install UFW manually.
After installing UFW, you need to enable the service by running the following command:
sudo systemctl enable ufw --nowThis command will enable the UFW service at boot time, ensuring your system remains protected after restarting.
Finally, it’s essential to verify the status of UFW to ensure it’s running without errors. You can check the status of the UFW service by running the following command:
systemctl status ufw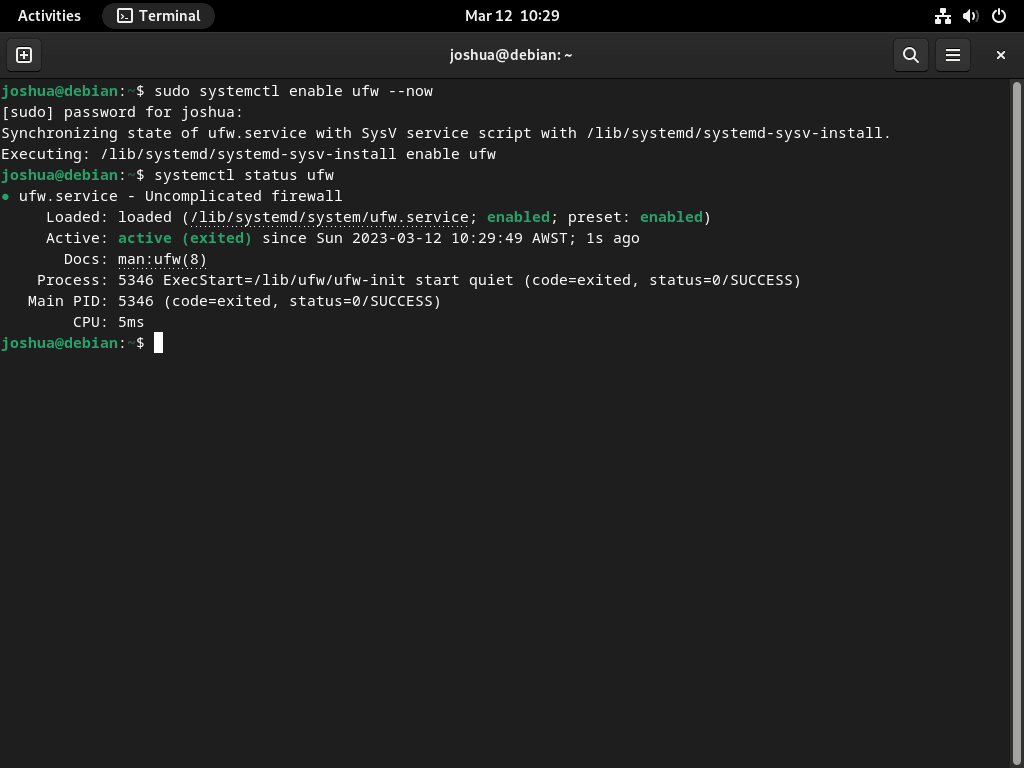
Running the commands above, you have successfully installed UFW and ensured it runs correctly. In the next step, we’ll explore using UFW to protect your system.
Enable UFW Firewall on Debian 12, 11 or 10
Now that UFW is installed and running, enabling the firewall is subsequent. By default, UFW blocks all incoming traffic and allows all outbound traffic. Enabling the firewall ensures that your system remains protected by blocking unauthorized access.
To enable UFW, run the following command:
sudo ufw enableAfter running the command, you’ll receive a confirmation message that the firewall is active and will start automatically whenever you restart your system. Here’s an example output:
Firewall is active and enabled on system startupOnce the firewall is active, it will block all incoming traffic to your system, protecting you from unauthorized access. However, it’s worth noting that this might also prevent some legitimate traffic, such as access to services that you need.
Check UFW Status on Debian 12, 11 or 10
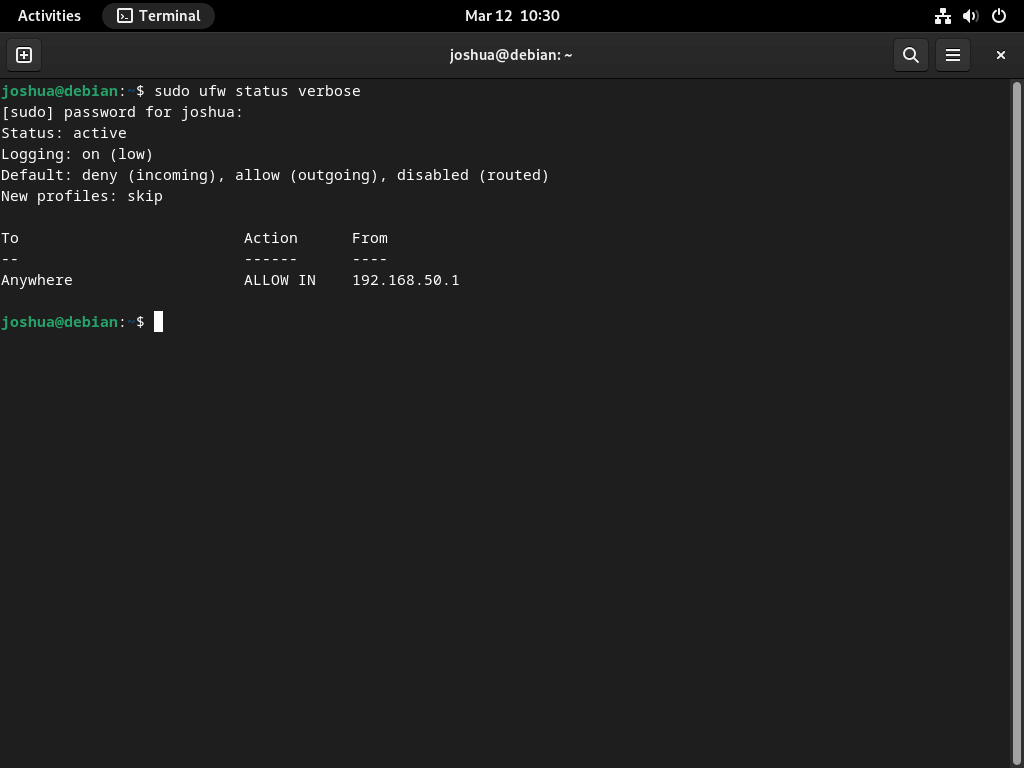
After enabling the UFW firewall, verifying that the rules are active and correctly configured is crucial. You can check the status of your firewall using the following command:
sudo ufw status verboseRunning this command will show you the current status of the firewall, including any active rules and the default policies set for incoming and outgoing traffic.
To get a more concise view of your firewall rules, you can use the “numbered” option instead. This option shows your firewall rules in a numbered sequence, making identifying and managing them easier. Use the following command to list your firewall rules in numbered sequence:
sudo ufw status numberedThe numbered output displays the rules in a more organized manner, making it easier to identify and manage them. You can use the rule numbers to modify or delete specific rules using the “delete” command.
In conclusion, verifying the status of your firewall is essential to ensure your system is protected from unauthorized access. Using the commands outlined in this step, you can quickly check the status of your UFW firewall and identify any misconfigurations.
Set UFW Default Policies on Debian 12, 11 or 10
The default setting of the UFW firewall is to block all incoming connections and allow all outbound connections. This configuration is the most secure as it ensures no unauthorized users can connect to your system without explicit permission. To allow incoming connections, you must create specific rules that permit traffic based on IP addresses, programs, ports, or a combination of these factors.
To modify the UFW rules, you can enter the following command in the terminal:
To deny all incoming connections:
sudo ufw default deny incomingTo allow all outgoing connections:
sudo ufw default allow outgoingBy default, UFW is already enabled with the default rules. However, you can modify these rules to suit your specific needs. For instance, if you want to block all outgoing connections and only allow specific outbound connections, you can use the following command to adjust the rules accordingly:
To block all outgoing connections:
sudo ufw default deny outgoingIt is worth noting that if you need to locate the default UFW firewall policies, you can find them in the /etc/default/ufw file. This file contains the configuration settings for UFW, including the default policies for incoming and outgoing traffic. By modifying the settings in this file, you can customize the firewall rules to meet your specific security needs.
Additional UFW Commands on Debian 12, 11 or 10
The following sections will cover some of the fundamental aspects of UFW. By default, most desktop users will benefit from simply blocking incoming connections and allowing all outgoing traffic, which is suitable for most environments. However, UFW provides additional configurations useful for desktops and servers. Some examples of what you can do with UFW will be shown below.
View UFW Application Profiles
If you’re interested in learning more about the application profiles available through UFW, you can view them by running the following command:
sudo ufw app listThis will display a list of all the available application profiles. It’s important to remember that the list of applications may vary depending on what software you have installed on your system.
One helpful feature of UFW application profiles is getting more information about a specific profile. To do this, run the following command:
sudo ufw app info [application]Replace [application] with the application name you want to learn more about. This command will provide a brief description of the application, as well as the ports it uses. This is helpful when investigating open ports and trying to determine what application they belong to.
Enable IPv6 on UFW
If your Debian system is configured with IPv6, you must ensure that UFW is configured to support IPv6 and IPv4 traffic. By default, UFW should automatically enable support for both versions of IP; however, it’s a good idea to confirm this.
To do so, open the default UFW firewall file using the following command:
sudo nano /etc/default/ufwOnce the file is open, locate the following line:
IPV6=yesIf the value is set to “no,” change it to “yes” and save the file by pressing CTRL+O and then CTRL+X to exit.
After making changes to the file, you’ll need to restart the UFW firewall service for the changes to take effect. To do so, run the following command:
sudo systemctl restart ufwThis will restart the UFW firewall service with the new configuration, enabling support for IPv6 traffic.
Allow UFW SSH Connections
SSH (Secure Shell) is crucial to remotely accessing Linux servers. However, by default, UFW does not allow SSH connections. This can be problematic, especially if you have enabled the firewall remotely, as you may find yourself locked out. To allow SSH connections, you need to follow these steps.
First, enable the SSH application profile by typing the following command:
sudo ufw allow sshIf you have set up a custom listening port for SSH connections other than the default port 22, for example, port 3541, you must open the port on the UFW firewall by typing the following.
sudo ufw allow 3541/tcpIf you want to block all SSH connections or change the port and block the old ones, you can do so using the following commands.
Use the following command to block all SSH connections (make sure local access is possible):
sudo ufw deny ssh/tcpIf changing the custom SSH port, open a new port and close the existing one, for example:
sudo ufw deny 3541/tcp Enable UFW Ports
UFW can allow access to specific ports for applications or services. In this section, we will cover how to open HTTP (port 80) and HTTPS (port 443) ports for a web server and how to allow port ranges.
To allow HTTP port 80, you can use any of the following commands:
Allow by application profile:
sudo ufw allow 'Nginx HTTPAllow by service name:
sudo ufw allow httpAllow by port number:
sudo ufw allow 80/tcpTo allow HTTPS port 443, you can use any of the following commands:
Allow by application profile:
sudo ufw allow 'Nginx HTTPS'Allow by service name:
sudo ufw allow httpsAllow by port number:
sudo ufw allow 443/tcpIf you want to allow both HTTP and HTTPS ports, you can use the following command:
sudo ufw allow 'Nginx Full'UFW Allow Port Ranges
In addition to allowing individual ports, you can also allow port ranges. When opening a port range, you must identify the port protocol.
To allow a port range with TCP and UDP protocols, use the following commands:
sudo ufw allow 6500:6800/tcp
sudo ufw allow 6500:6800/udpAlternatively, you can allow multiple ports in one hit using the following commands:
sudo ufw allow 6500, 6501, 6505, 6509/tcp
sudo ufw allow 6500, 6501, 6505, 6509/udpAllow Remote Connections on UFW
Enabling remote connections on UFW can be crucial for networking purposes, and it can be done quickly with a few simple commands. This section explains how to allow remote connections to your system through UFW.
UFW Allow Specific IP Addresses
You can use the following command to allow specific IP addresses to connect to your system. This is useful when you need to allow only specific systems to connect to your server, and you can specify their IP addresses.
sudo ufw allow from 192.168.55.131UFW Allow Specific IP Addresses on Specific Port
You can use the following command if you need to allow an IP to connect to a specific port on your system. For instance, if you need to allow an IP to connect to your system’s port 3900, you can use this command:
sudo ufw allow from 192.168.55.131 to any port 3900Allow Subnet Connections to a Specified Port
You can use the following command to allow connections from a range of IPs in a subnet to a specific port. This is useful when you need to allow connections from a specific range of IPs, and you can specify the subnet to allow connections.
sudo ufw allow from 192.168.1.0/24 to any port 3900This command will connect all IP addresses from 192.168.1.1 to 192.168.1.254 to port 3900.
Allow Specific Network Interface
If you need to allow connections to a specific network interface, you can use the following command. This is useful when you have multiple network interfaces and need to allow connections to a specific interface.
sudo ufw allow in on eth2 to any port 3900By using these commands, you can easily allow remote connections to your system through UFW while maintaining the security of your system.
Deny Remote Connections on UFW
If you’ve noticed suspicious or unwanted traffic coming from a particular IP address, you can deny connections from that address using UFW. UFW denies all incoming connections by default, but you can create specific rules to block connections from specific IPs or IP ranges.
For example, to block connections from a single IP address, you can use the following command:
sudo ufw deny from 203.13.56.121If a hacker is using multiple IP addresses within the same subnet to attack your system, you can block the entire subnet by specifying the IP range in CIDR notation:
sudo ufw deny from 203.13.56.121/24You can also create rules to deny access to specific ports for the blocked IP or IP range. For example, to block connections from the same subnet to ports 80 and 443, you can use the following commands:
sudo ufw deny from 203.13.56.121/24 to any port 80
sudo ufw deny from 203.13.56.121/24 to any port 443It’s important to note that blocking incoming connections can be an effective security measure, but it’s not foolproof. Hackers can still use techniques like IP spoofing to disguise their true IP address. Therefore, it’s important to implement multiple layers of security and not rely solely on IP blocking.
Delete UFW Rules
Deleting unnecessary or unwanted UFW rules is essential for maintaining an organized and efficient firewall. You can delete UFW rules in two different ways. Firstly, to delete a UFW rule using its number, you need to list the rule numbers by typing the following command:
sudo ufw status numberedThe output will display a list of numbered UFW rules, allowing you to identify the rule you want to delete. Once you have determined the number of the rule you wish to remove, type the following command:
sudo ufw delete [rule number]For instance, suppose you want to delete the third rule for IP Address 1.1.1.1. In that case, you need to find the rule number by running the “sudo ufw status numbered” command and type the following command in your terminal:
sudo ufw delete 3Deleting rules that are no longer required helps to maintain the security and efficiency of your firewall.
Access and View UFW Logs
The UFW firewall logs all events, and it is essential to review these logs periodically to identify potential security breaches or troubleshoot network issues. UFW logging is set to low by default, which is adequate for most desktop systems. However, servers may require a higher level of logging to capture more details.
You can adjust the logging level of UFW to low, medium, or high or disable it entirely. To set the UFW logging level to low, use the following command:
sudo ufw logging lowTo set UFW logging to medium:
sudo ufw logging mediumTo set UFW logging to high:
sudo ufw logging highThe last option is to disable logging altogether; be sure you are happy with this, and it will not require log checking.
sudo ufw logging offTo view UFW logs, you can find them in the default location of /var/log/ufw.log. You can view live logs or print out a specified number of recent log lines using the tail command. For instance, to view the last 30 lines of the log, use the following command:
sudo ufw tail /var/log/ufw.log -n 30
Reviewing the logs, you can determine which IP addresses are attempting to connect to your system and identify any suspicious or unauthorized activities. Furthermore, reviewing the logs can help you understand network traffic patterns, which can help you optimize network performance and identify any issues that may arise.
Test UFW Rules
Testing your UFW firewall rules before applying them to ensure they work as intended is always a good idea. The “–dry-run” flag allows you to see the changes that would have been made without actually applying them. This is a helpful option for highly critical systems to prevent accidental changes.
To use the “–dry-run” flag, type the following command:
sudo ufw --dry-run enableTo disable the “–dry-run” flag, simply use the following command:
sudo ufw --dry-run disableReset UFW Rules
Sometimes, you may need to reset your firewall back to its original state with all incoming connections blocked and outgoing connections allowed. This can be done using the “reset” command:
sudo ufw resetConfirm reset, enter the following:
sudo ufw statusThe output should be:
Status: inactive Once the reset is complete, the firewall will be inactive, and you will need to re-enable it and start adding new rules. It is important to note that the reset command should be used sparingly, as it removes all existing rules and can potentially leave your system vulnerable if not done correctly.
How to find All Open Ports (Security Check)
The security of your system should be a top priority and one way to ensure it is by checking for open ports regularly. UFW blocks all incoming connections by default, but sometimes, ports may be left open inadvertently or for legitimate reasons. In this case, knowing which ports are open and why is essential.
One way to check for open ports is using Nmap, a well-known and trusted network exploration tool. To use Nmap, install it first by typing the following command.
sudo apt install nmapNext, find your system’s internal IP address by typing:
hostname -IExample output:
192.168.50.45With the IP address, run the following command:
nmap 192.168.50.45Nmap will scan your system and list all open ports. If you find any open ports you are unsure about, investigate them before closing or blocking them, as it may break services or lock you out of your system.
You can create custom UFW rules you learned in this tutorial to close or restrict open ports. UFW blocks all incoming connections by default, so ensure you are not blocking legitimate traffic before implementing any changes.
UFW Management Commands on Debian 12, 11 or 10
Remove the UFW Firewall From Debian
UFW is a valuable tool to manage firewall rules and secure your Debian system. However, there may be situations where you need to disable or remove UFW.
If you want to disable UFW temporarily, you can do so by typing the following command:
sudo ufw disableThis will turn off the firewall, allowing all traffic to pass through the system.
On the other hand, if you need to remove UFW from your system altogether, you can do so with the following command:
sudo apt remove ufwHowever, it’s essential to note that removing UFW altogether from your system may leave it vulnerable to external attacks. Unless you have a solid alternative to manage your system’s firewall or understand how to use IPTables, it’s not advisable to remove UFW.
Therefore, before removing UFW, ensure you have an alternative solution to maintain your system’s security and prevent unauthorized access.
Conclusion
It is essential to install and set up the UFW firewall on Debian to safeguard your system against harmful assaults. This measure should be taken regardless of the environment you operate in, as long as you are connected to any internal or external network.