Nginx, often pronounced as “Engine X”, stands as a beacon of efficiency and versatility in web servers. For those aiming to install Nginx on Debian 12 Bookworm, Debian 11 Bullseye, or Debian 10 Buster, it’s essential to grasp its multifaceted capabilities. Originating from the vision of Igor Sysoev in 2002, Nginx was crafted with an emphasis on performance, stability, and minimal resource consumption. Today, it’s not just a web server but also a reverse proxy, load balancer, mail proxy, and HTTP cache.
Key Features of Nginx:
- Web Server: At its core, Nginx serves web content, responding to requests for HTML pages and associated assets from web browsers.
- Reverse Proxy: Nginx can act as an intermediary, forwarding client requests to other web servers, adding a layer of control and abstraction for optimized network traffic flow.
- Load Balancer: Efficiently distributes incoming network or application traffic across multiple servers, ensuring balanced resource usage and high availability.
- HTTP Cache: Nginx caches responses from a web server, reducing the need to fetch the same content from the original server for subsequent requests.
- Mail Proxy: Beyond web content, Nginx can forward email requests to multiple recipients, offering functionalities like load balancing and spam filtering.
Nginx’s multifunctional nature, efficiency, and reliability make it a top choice for many web professionals. Whether setting up a personal website or managing a large-scale web application, Nginx offers the necessary tools and performance. The subsequent sections will guide you through the steps to install Nginx on Debian 12 Bookworm, Debian 11 Bullseye, or Debian 10 Buster, ensuring a seamless setup process.
Install Nginx on Debian 12, 11, or 10 via APT
Step 1: Preparing Your System Before Nginx Installation
Ensure your system is updated before installing Nginx. This prevents potential conflicts during the installation and reduces the risk of compatibility issues and security vulnerabilities.
To update your system packages, run the following:
sudo apt update && sudo apt upgradeThis command fetches the list of available updates (via apt update) and then upgrades the current software packages to their latest versions (using apt upgrade).
Step 2: Install NGINX’ Web Server’ standard on Debian
By default, NGINX is available in the Debian repositories. This makes the installation process straightforward.
Run the following command to install nginx:
sudo apt install nginxThe apt install command tells APT package handling utility (a part of the Debian system) to install the NGINX package.
Optional: Install the NGINX-Full Version
NGINX offers a nginx-full version with additional modules not found in the standard version. If you require more functionality, install the nginx-full version:
sudo apt install nginx-fullOptional: Install the NGINX-Extras Version
For an even broader feature set, consider the nginx-extras version. To install:
sudo apt install nginx-extrasStep 3: Verifying the NGINX Installation on Debian
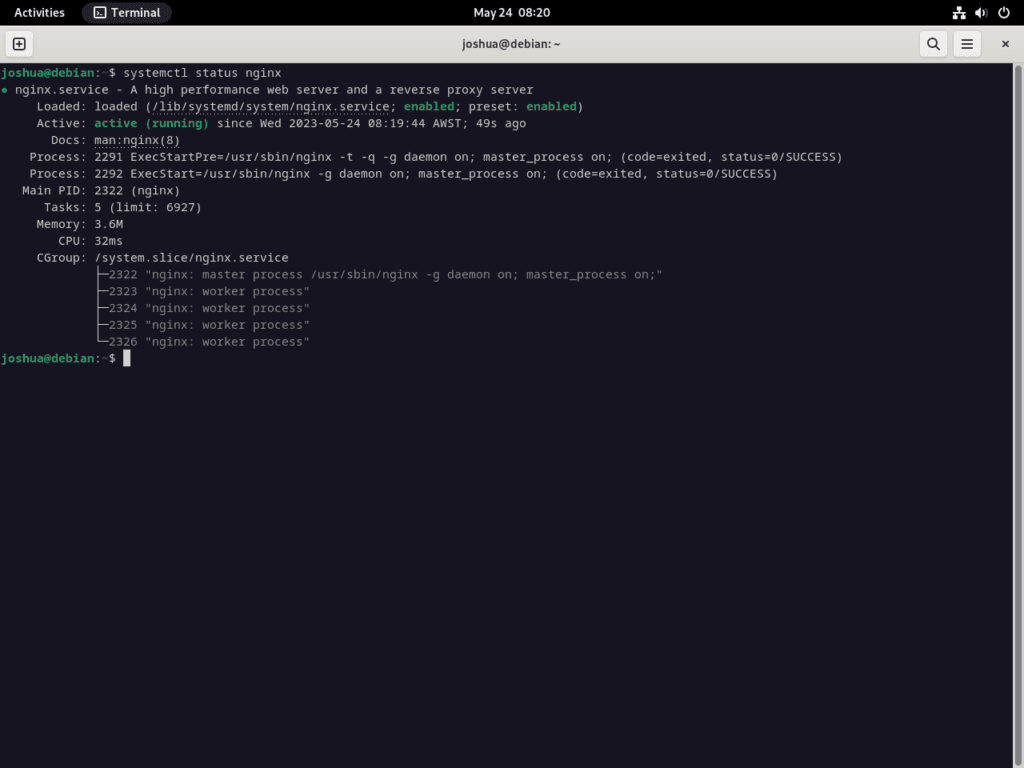
After installation, ensure NGINX is running correctly.
Check the NGINX service status with the following:
systemctl status nginxNGINX is operating correctly if the output shows “active (running)”. If not, the output will detail the error for troubleshooting.
If NGINX isn’t enabled, use:
sudo systemctl enable nginx --nowConfigure UFW Firewall For Nginx on Debian 12, 11 or 10
Step 1: Introduction to UFW
UFW, or Uncomplicated Firewall, provides an easy-to-use interface for managing iptables firewall rules. It’s not installed on Debian by default, but you can get it from the default repositories. If your server has public access, you should set up UFW rules for security.
Step 2: Install UFW
If UFW isn’t already installed on your system, you can do so by executing the following command:
sudo apt install ufwStep 3: Enable UFW
Once the installation is complete, you can enable UFW by running the following command:
sudo ufw enableUFW’s default settings block all incoming connections and allow all outgoing ones. This means it stops unsolicited system access but lets your system reach the outside world.
Step 4: Listing Installed Applications
UFW uses application profiles, which are sets of rules for specific applications. To see installed applications that have UFW profiles, run:
sudo ufw app listStep 5: Configuring UFW Rules for NGINX
Depending on your needs, you can configure UFW to let NGINX connections through HTTP (Port 80), HTTPS (Port 443), or both.
For HTTP (Port 80) only:
sudo ufw allow 'Nginx HTTP'HTTPS (Port 443) only:
sudo ufw allow 'Nginx HTTPS'Both HTTP and HTTPS:
sudo ufw allow 'Nginx Full'Step 6: Verifying Firewall Rules
To confirm your rules are in place, check the active firewall rules:
sudo ufw statusStep 7: Testing NGINX Configuration
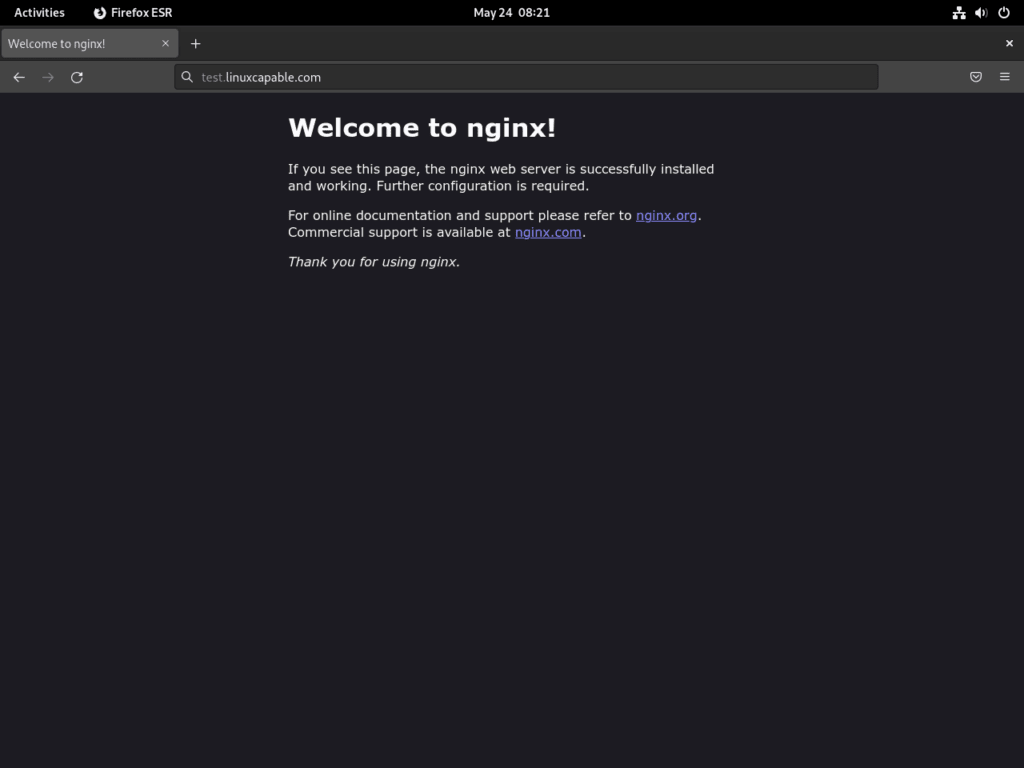
After setting up UFW, ensure you can see the NGINX landing page. In your browser, go to your server’s IP address:
http://your_server_ipOr, for local setups:
http://localhostIf you see the NGINX default page, your configuration works. This ends the firewall setup for NGINX on Debian.
Create NGINX Server Blocks on Debian 12, 11 or 10
Step 1: Introduction to NGINX Server Blocks
Like Apache’s virtual hosts, NGINX server blocks let you host multiple domains from one server. Each domain has its configuration settings. For this guide, replace “example.com” with your actual domain name.
Step 2: Create a Directory for Your Domain
Set up a directory for your domain. This directory will store your website’s files:
sudo mkdir -p /var/www/example.com/Step 3: Assign Ownership to the Nginx Directory
Assign directory ownership to the “www-data” user and group, which NGINX usually uses:
sudo chown -R www-data:www-data /var/www/example.com/Step 4: Create a Nginx Test HTML Page on Debian
Create a test HTML page in your domain directory to confirm your NGINX setup:
sudo nano /var/www/example.com/index.htmlAdd the following HTML code:
<html>
<head>
<title>Welcome to Example.com</title>
</head>
<body>
<h1>Success! The NGINX server block is working!</h1>
</body>
</html>
After you’ve pasted the code into the nano editor, press CTRL+O to save the changes and then CTRL+X to exit the editor.
Step 5: Create an NGINX Server Block For Test Page
Set up a server block for your website:
sudo nano /etc/nginx/sites-available/example.com.confAdd the following configuration:
server {
listen 80;
listen [::]:80;
root /var/www/example.com/;
index index.html index.htm index.nginx-debian.html;
server_name example.com www.example.com;
location / {
try_files $uri $uri/ =404;
}
}
This configuration tells NGINX to listen for incoming connections on port 80 for both example.com and www.example.com. Be sure to replace the root directive with the directory path you created earlier.
Step 6: Enable the NGINX Server Block via symlink
Enable your server block by creating a symbolic link from the sites-available directory to the sites-enabled directory:
sudo ln -s /etc/nginx/sites-available/example.com.conf /etc/nginx/sites-enabled/Step 7: Final Configuration & Test Run
Lastly, we’ll edit the default NGINX configuration file and perform a test run to ensure everything works as expected.
Editing the NGINX Configuration File
Open the nginx.conf file:
sudo nano /etc/nginx/nginx.confLook for the line server_names_hash_bucket_size 64; within the http {} block and uncomment it.
This directive allows NGINX to handle long domain names and more significant numbers of server names by allocating more memory for this purpose. However, be cautious not to set this value too high, as it might consume more memory than needed.
Save the changes and exit the editor by pressing CTRL+O and CTRL+X.
Test Your NGINX Configuration
Before you go ahead and restart NGINX, it’s a good practice to verify that your configuration syntax is correct. Run the following command to initiate a test run:
sudo nginx -tIf your configuration is correct, you’ll see this output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
These messages indicate that your NGINX configuration has been successfully validated.
Verifying Your Server Block
To ensure your server block functions appropriately, open your domain in a web browser. You should see the test page confirming your server block is active.
Additional Nginx Commands & Tips on Debian 12, 11 or 10
Enhancing File Security in Your Webserver
Security for files and folders on your web server is paramount. Avoid overly permissive access rights. Set correct permissions for all files and directories in your webroot using these commands. Remember to replace /var/www/example.com/ with your webroot path:
sudo find /var/www/example.com/ -type d -exec chmod 755 "{}" \;
sudo find /var/www/example.com/ -type f -exec chmod 644 "{}" \;These commands set read and execute permissions for directories and read-write permissions for files for the owner. Groups and others get read-only access. Adjust these permissions as your application demands.
Nginx Security with Let’s Encrypt Free SSL Certificate
Using HTTPS protocol ensures web server security. Let’s Encrypt provides a free SSL certificate. Install the certbot package with:
sudo apt install python3-certbot-nginxThen, initiate the certificate creation:
sudo certbot --nginx --agree-tos --redirect --hsts --staple-ocsp --email you@example.com -d www.example.comReplace with your email and domain name. This command sets up HTTPS with the required security features.
Setting Up Automatic Certificate Renewal
Let’s Encrypt certificates last 90 days. Set up automatic renewals with the Certbot script. Test the process:
sudo certbot renew --dry-runIf successful, add the renewal command to crontab:
sudo crontab -eInclude this line to renew daily at midnight:
00 00 */1 * * /usr/sbin/certbot-auto renewNginx Server Logs
Monitor your server logs for a well-maintained web server. By default, logs reside in /var/log/nginx. List them with:
cd /var/log/nginx && ls -lThe most relevant log files are the access.log and error.log. To monitor logs in real-time, use the tail -f command followed by the path to the log:
tail -f /var/log/nginx/access.logUpdate Nginx
Before updating your Nginx server, creating a backup of your current configurations is wise. To back up your main nginx.conf file, use the following command:
sudo cp /etc/nginx/nginx.conf /etc/nginx/nginx-backup.confIn cases where you have extensively customized your Nginx setup, you might want to back up your entire Nginx directory:
sudo cp -r /etc/nginx/ /etc/nginx-bkupWith your configurations safely backed up, you can now proceed to update Nginx:
sudo apt update
sudo apt upgradeRegularly backing up your configurations is good practice, especially in complex setups.
Remove Nginx
In the event that you no longer need Nginx on your server, you can remove it by following these steps. First, ensure that the Nginx service is stopped:
sudo systemctl disable nginx --nowNext, altogether remove the Nginx package:
sudo apt remove nginxYou may still find remnants of Nginx configurations in the /etc/nginx directory. To remove these, use the command:
sudo rm -R /etc/nginx/Remember that this will remove all your custom configuration files, so ensure you have everything you need backed up before proceeding with this step.
Configure Log Rotation Parameters in Nginx on Debian
Nginx includes a daily log rotation feature by default. However, Nginx allows you to customize these settings based on your needs.
Access Configuration File for Log Rotation
To modify the log rotation settings, you need to access the configuration file. Here’s how you can open it using the nano text editor:
sudo nano /etc/nginx/logrotate.d/nginxOnce you open the file, you’ll see content resembling the following. Adjust the directives in this file to fit your log retention and rotation needs, mainly if you use monitoring tools like fail2ban.
Sample Log Rotation Configuration File
/var/log/nginx/*.log {
daily
missingok
rotate 14
compress
delaycompress
notifempty
create 0640 www-data adm
sharedscripts
prerotate
if [ -d /etc/logrotate.d/httpd-prerotate ]; then \
run-parts /etc/logrotate.d/httpd-prerotate; \
fi \
endscript
postrotate
invoke-rc.d nginx rotate >/dev/null 2>&1
endscript
}Understanding Primary Configuration Parameters
Within this configuration, system administrators typically focus on two main settings:
- Daily: This setting sets the log rotation frequency. While it defaults to ‘daily’, you can change it to ‘weekly’ or ‘monthly’. But daily rotations typically simplify log management.
- Rotate 14: This number tells the system how many log files to keep. For example, a setting of ’14’ retains the 14 latest logs. If you want to store only a week of logs, adjust this number to ‘7’.
While Nginx lets you modify other settings, always make changes with care. Changing settings without understanding their impact can cause unexpected results. Ensure you modify these settings to suit your needs without causing unintended issues.
Remember, there’s no one-size-fits-all approach to log management. Always assess your specific environment and requirements before making changes.
Closing Thoughts
This guide explored how to install and adjust Nginx on Debian Linux. We started by highlighting Nginx’s advantages, making it a top choice for many experts. We then discussed the installation steps in detail. Additionally, we touched on how to customize Nginx, especially the log rotation settings. Knowing how to control these settings can make your system management tasks easier and boost efficiency.
This guide showcases Nginx’s adaptability to various needs. Keep in mind that this guide is just the beginning. True expertise comes from ongoing learning and practical experience, like any technical skill.