You’re in the right place if you aim to install Apache on Debian 12 Bookworm or the older stable releases of Debian 11 Bullseye or Debian 10 Buster. Apache HTTP Server, often called Apache, is a leading web server software known for its reliability, versatility, and robustness. As the foundation for many websites and web applications, Apache has solidified its position as a cornerstone in the digital domain.
Key Highlights of Apache:
- Widespread Adoption: Apache’s trusted performance has led to its adoption by many websites globally.
- Modular Architecture: Apache offers a modular architecture, allowing users to extend its features easily.
- Versatility: It can handle various web hosting needs, from basic websites to intricate web applications.
- Stability: Known for its consistent uptime, Apache ensures websites remain accessible without frequent downtimes.
- Security: Regular updates and a dedicated community mean that Apache is equipped to handle emerging security threats.
- Customization: With many modules available, users can customize Apache to meet specific requirements.
This guide will now delve into the process and benefits of installing Apache, emphasizing its significance in the digital realm.
Install Apache (HTTPD) on Debian 12, 11 or 10
Step 1: Update Debian Packages Before Apache Installation
The initial step in setting up Apache on your Debian system involves updating the system’s packages. This is an essential procedure that ensures all the existing packages in your system are up to date.
To accomplish this, you would need to open your system terminal and input the following command:
sudo apt update && sudo apt upgradeStep 2: Install Apache via APT Command on Debian
With your system updated, you can proceed with the Apache installation. Like many other Linux distributions, Debian provides a default repository of software packages from which you can easily install Apache.
To perform the installation, return to your terminal and type in the following command:
sudo apt install apache2Again, sudo is used to run the command with administrative privileges. apt install apache2 is the actual command that instructs the system to find the apache2 package in its repositories and install it.
Step 3: Verifying the Apache Installation
Upon successful installation of Apache, it’s always good practice to verify that everything was correctly set up. The first method to do this is by checking Apache’s version number. This helps you ascertain that the correct version of Apache was installed.
Use the following command in the terminal to check Apache’s version:
apache2 --versionThis command returns the installed version of Apache, which confirms that the installation process was completed successfully.
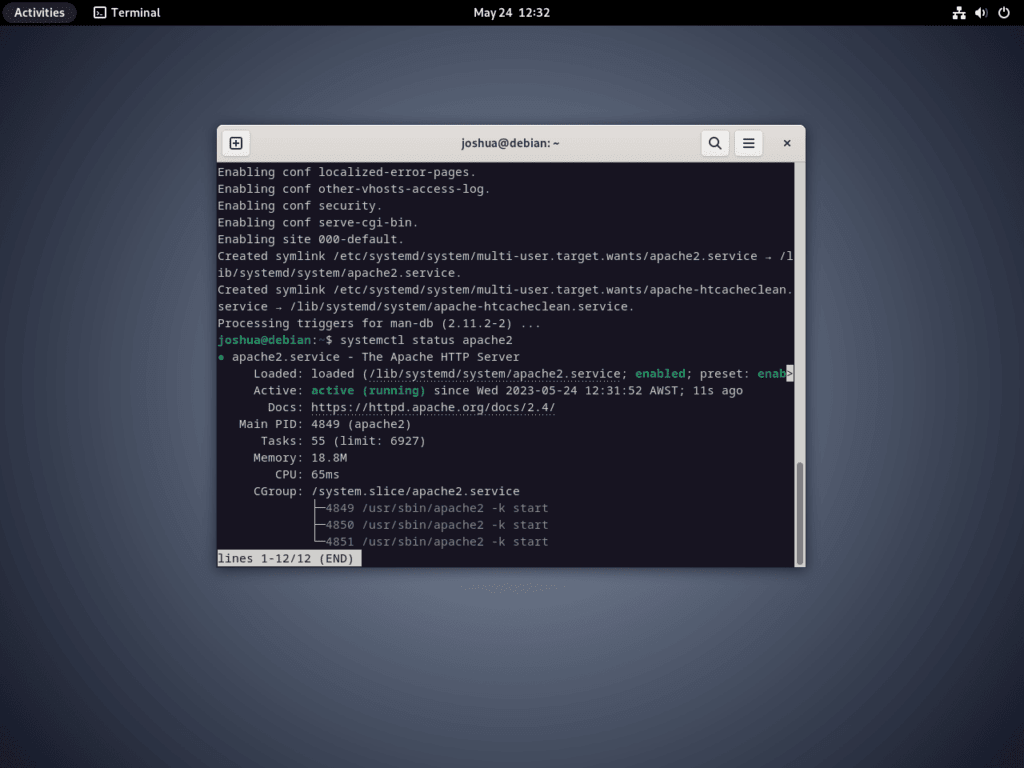
Another method to verify the installation involves checking Apache’s service status using systemd, the system and service manager for Linux operating systems. This is essential to ensure that the Apache service is running correctly.
You can check the systemd status with the following command:
systemctl status apache2The system will return inactive if Apache’s service isn’t running. To rectify this, you can initiate the Apache service and enable it to start on the system boot using the following command:
sudo systemctl enable apache2 --nowThis command sets Apache to automatically start each time your system boots, ensuring continuous, uninterrupted operation of your web server. The --now flag starts the service immediately after enabling it.
Once this is done, your Apache HTTPD Web Server should be up and running, ready for configuration to host your websites and web applications.
Configure UFW Firewall for Apache on Debian 12, 11 or 10
Step 1: Understanding UFW
The well-known Uncomplicated Firewall, or UFW, is an intuitive interface for managing iptables firewall rules. Its design makes it highly accessible and straightforward, even for those new to firewall configurations. Although UFW isn’t preinstalled on Debian, it’s readily available from the default software repositories. This tool is an essential asset, especially if your server is open to public access, as configuring UFW rules plays a significant role in maintaining your server’s security.
Step 2: Install UFW on Debian
If UFW isn’t on your system, the installation is just a terminal command away. The following command instructs the APT package handling utility (the standard tool on Debian for handling packages) to install the UFW package:
sudo apt install ufw -yHere, the -y flag is used to automate the process by automatically saying yes to the prompts and running non-interactively.
Step 3: Activating UFW on Debian
With UFW successfully installed, the next step is to activate it. This is done using the following command:
sudo ufw enableBy default, UFW blocks all incoming connections while allowing all outgoing connections. This configuration provides a basic security level, as it helps to deter unsolicited access to your system but still allows your system to communicate with the outside world.
Step 4: Checking Installed Applications UFW Profiles
UFW comes with a feature known as application profiles. These are pre-defined rules that can be easily applied to specific applications. To see the list of installed applications that have UFW profiles, use the following command:
sudo ufw app listStep 5: Setting UFW Rules for Apache
Depending on your requirements, you can set UFW to allow connections to Apache on HTTP (Port 80), HTTPS (Port 443), or both. The rules can be configured using these commands:
To allow HTTP (Port 80) only:
sudo ufw allow 'Apache Full'HTTPS (Port 443) only, use the following:
sudo ufw allow 'Apache Secure'Both HTTP and HTTPS:
sudo ufw allow 'Apache Full' && sudo ufw allow 'Apache Secure'Step 6: Verifying UFW Firewall Rules
After setting up the rules, confirming they have been correctly implemented is essential. The following command lets you verify the currently active firewall rules:
sudo ufw statusThis command displays the status of UFW and the rules currently in effect.
Step 7: Testing Apache Configuration
After configuring UFW, ensuring you can access the Apache default page is essential. In your web browser, navigate to your server’s IP address:
http://your_server_ipFor local installations, you can try accessing the localhost:
http://localhostYou should see the Apache default landing page if everything was set up correctly.
Create Virtual Hosts for Apache on Debian 12, 11, or 10
Virtual hosts in Apache are vital, enabling you to manage configurations for multiple domains on a single server. Think of virtual hosts as analogous to server blocks in Nginx. This section will guide you through setting up a virtual host for a domain, which we’ll refer to as “example-domain.com.” Please replace this with your actual domain name as you follow along.
Step 1: Create and Set Permission for Apache Directories
In a fresh Debian installation with Apache, you’ll find a single server block enabled by default, designed to serve documents from the /var/www/html directory. If you’re only hosting a single website, this default server block might suffice with some modifications. However, creating a unique directory structure for your various domains is prudent if you plan to host multiple websites.
Let’s keep the /var/www/html directory untouched as our default directory. We’ll create a fresh directory for our example-domain.com. Here’s how to do it:
sudo mkdir /var/www/example_domainAfter creating the directory, we need to assign ownership to it using the $USER environment variable like so:
sudo chown -R $USER:$USER /var/www/example_domainIt’s essential to set the correct permissions for the web root. You can verify the permissions using the ls -l command:
ls -l /var/www/An exemplary output would look like:
drwxr-xr-x 2 joshua joshua 4096 Apr 18 15:25 example_domain
drwxr-xr-x 2 root root 4096 Apr 18 15:23 htmlThe permissions of drwxr-xr-x are equivalent to chmod 755. If your permissions do not match this, run the following command:
sudo chmod -R 755 /var/www/example_domainNext, let’s create a sample index.html page using the nano text editor:
<html>
<head>
<title>Welcome to Website!</title>
</head>
<body>
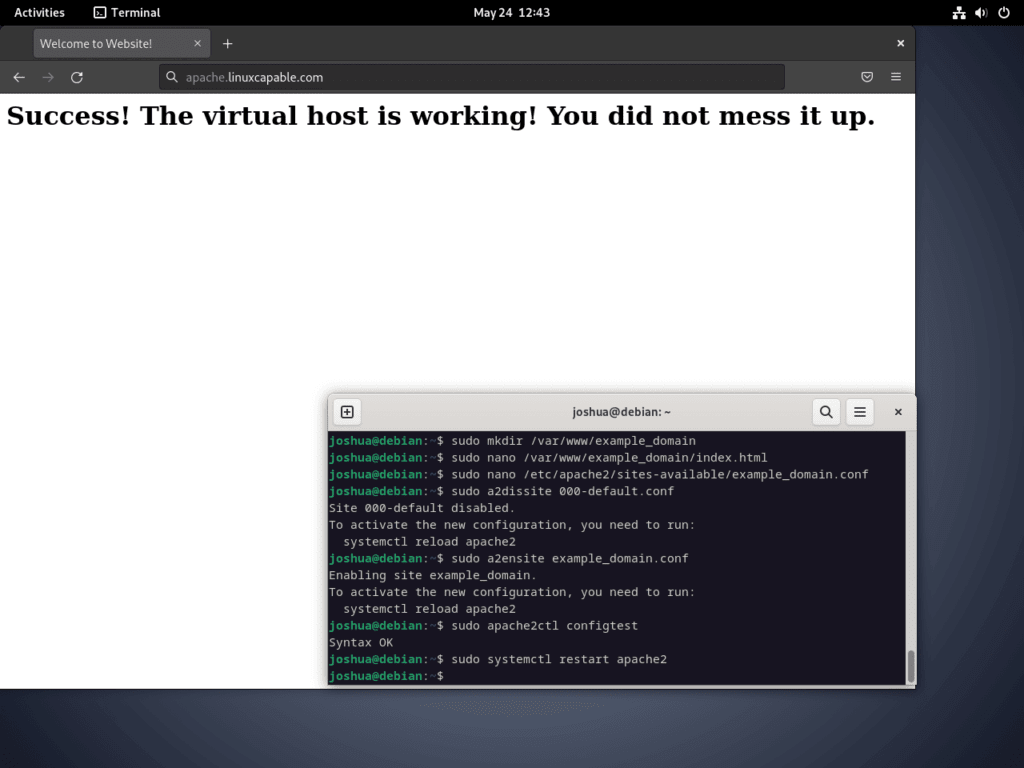
<h1>Success! The virtual host is working! You did not mess it up.</h1>
</body>
</html>After writing, save the file (CTRL+O), then exit (CTRL+X).
Step 2: Create a Virtual Host For Apache on Debian
With the landing page created and the correct ownership and permissions set, you’re now ready to create a virtual host file. Apache expects virtual host files to be located in the /etc/apache2/sites-available/ directory.
Use your preferred text editor to create a configuration file at /etc/apache2/sites-available/example_domain.conf:
sudo nano /etc/apache2/sites-available/example_domain.confIn this configuration file, paste the following block, ensuring you replace ServerName, ServerAlias, and DocumentRoot with your own:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
ServerName example_domain
ServerAlias www.example_domain
DocumentRoot /var/www/example_domain
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>Remember to modify the required server directives to match your setup.
After setting the configuration, save the file (CTRL+O) and exit (CTRL+X).
Step 3: Activate the Apache Virtual Host
With your virtual host configuration file primed and ready, it’s time to enable it. Unlike Nginx, where you’d create a symbolic link using the ln -s command, Apache employs its own set of tools to handle this task.
First, disable the existing default server block file 000-default.conf with the a2dissite command:
sudo a2dissite 000-default.confNext, enable your newly created virtual host file using the a2ensite command:
sudo a2ensite example_domain.confApache also comes with a helpful feature known as a dry run. Before going live with your new configuration, it’s a good practice to test it using the following command:
sudo apache2ctl configtestIf everything is configured correctly, the output should look like:
Syntax OKFinally, restart the Apache webserver to activate your new virtual host using the following command:
sudo systemctl restart apache2Apache should serve the landing page you created for your new domain. To verify this, open your web browser and type in your domain name http://example_domain, and you should be able to view the landing page you crafted in the index.html file.
Create Let’s Encrypt’s Free SSL Certificate For Apache on Debian 12, 11, or 10
In web hosting, securing your website can’t be overstated. Employing an SSL/TLS certificate to run your Apache web server over HTTPS is an essential step to bolster the privacy and security of your website. A leading choice for this purpose is Let’s Encrypt, a free, automated, and open certificate authority from the nonprofit Internet Security Research Group (ISRG).
Step 1: Install the Apache Certbot Package
The first step towards securing your website is to install the certbot package. This handy tool automates procuring and installing SSL/TLS certificates from Let’s Encrypt. The following command should do the trick:
sudo apt install python3-certbot-apache -yStep 2: Generating and Setting Up the SSL Certificate
With certbot successfully installed, it’s time to generate your SSL/TLS certificate and link it with your Apache web server. Here’s the command you’ll need to use:
sudo certbot --apache --agree-tos --redirect --hsts --staple-ocsp --email you@example.com -d www.example.com
This command encompasses several options, namely:
- Enforcing HTTPS 301 redirects (
--redirect) - Implementing the Strict-Transport-Security header (
--hsts) - Enabling OCSP Stapling (
--staple-ocsp)
Substitute the placeholder email address and domain name with your actual information.
Step 3: Validating SSL Configuration
Upon successful execution of the previous steps, the URL of your website should now begin with https://www.example.com instead of http://www.example.com. Anyone who tries to access your website using the old HTTP URL will automatically be redirected to HTTPS, thus ensuring a secure connection.
To ascertain that the SSL configuration is active, visit your website and look for the padlock symbol in your browser’s address bar. This symbol indicates that the connection to your website is secure and encrypted.
Step 4: Automating SSL Certificate Renewal
It’s worth noting that the certificates issued by Let’s Encrypt have a validity period of 90 days. Therefore, it’s crucial to establish an automated renewal process. By default, Certbot incorporates either a cron job or systemd timer to manage renewals automatically.
To manually verify the renewal process, you can run the following command:
sudo certbot renew --dry-runThis command conducts a dry run of the renewal process, testing whether the renewal will function without actually renewing the certificate. If the test is successful, it’s a reassuring indication that your certificate will be renewed automatically before its expiration.
Monitoring Your Apache Service on Debian 12, 11 or 10
Managing a web server does not end with its setup and securing it with SSL/TLS. It’s vital to continuously monitor your server to ensure optimal performance, detect potential issues, and fix them promptly.
Installing and Configuring Apache’s mod_status
Apache provides a handy module called mod_status that offers information on your server’s performance. If it’s not already enabled, you can activate it using the following command:
sudo a2enmod statusThe mod_status module provides a web page that contains statistics about the server’s operation. You can access this page to monitor server activity in real time. To make the status page accessible, you’ll need to edit the configuration file for the module:
sudo nano /etc/apache2/mods-enabled/status.confYou should see a configuration block like the following:
<Location /server-status>
SetHandler server-status
Require local
</Location>This block restricts access to the server status page to local connections. If you want to allow access from other locations, replace Require local with Require all granted. Save the file (CTRL+O), then exit (CTRL+X).
Checking Apache Server Status
With mod_status activated and configured, you can access the server status page by navigating to http://your_server_IP/server-status.
The status page offers information like:
- The number of worker serving requests
- The number of idle worker
- The current CPU usage
- Details about the requests being processed
Configuring Apache Log Files
Apache keeps comprehensive logs, offering a wealth of information about what’s happening on your server. By default, Apache keeps two log files:
- Access log (
/var/log/apache2/access.log): Records every page served and every file loaded by the web server. - Error log (
/var/log/apache2/error.log): Records all errors encountered in processing requests.
Monitoring these logs can provide insights into server performance and potential issues, which will discussed in more detail in the next section.
Tips For Managing Your Apache Web Server on Debian 12, 11, or 10
In the previous sections, we’ve learned how to set up, secure, and monitor your Apache web server. Now, it’s time to delve into managing your Apache server. Key server management aspects include understanding server logs and mastering Apache commands for effective daily operation.
Understanding Apache Server Logs
Apache logs are crucial for diagnosing issues, overseeing user activity, and acquiring insights about your server’s performance. Logs can track server errors, identify potential security threats, and monitor user activities. They are a treasure trove of information, provided you know how to utilize them effectively. Let’s look at a few examples of Linux commands that can peruse and analyze Apache logs.
Review Recent Log Entries
Using the tail command, you can check the most recent entries of a log file. This command is handy for inspecting recent activities or errors. The following commands display the last ten lines of the access and error logs:
tail /var/log/apache2/access.log
tail /var/log/apache2/error.logMonitor Logs in Real-Time
The tail -f command is used to view log files in real time, a handy tool for observing ongoing user activities or troubleshooting problems as they transpire.
tail -f /var/log/apache2/access.log
tail -f /var/log/apache2/error.logKeyword Searches in Log Files
The grep command is used for searching specific keywords or patterns within log files. For instance, you can search for the occurrence of the “404” error code in the error log:
grep "404" /var/log/apache2/error.logCount Keyword Occurrences
grep, combined with the -c flag, can be used to tally the number of times a particular keyword or pattern appears in log files. For example, to count the number of “500” error codes in the error log:
grep -c "500" /var/log/apache2/error.logIdentify Unique IP Addresses Accessing the Server
The awk command can be used to list unique IP addresses that have accessed your server by analyzing the access log:
awk '{print $1}' /var/log/apache2/access.log | sort | uniqYou can use Linux commands to explore and analyze Apache logs in several ways.
Familiarizing with Basic Apache Commands
Below are some of the most commonly used Apache commands you’ll likely need for routine management of your Apache web server:
Stopping the Apache Web Server:
sudo systemctl stop apache2Starting the Apache Web Server:
sudo systemctl start apache2Restarting the Apache Web Server:
sudo systemctl restart apache2Reloading the Apache Web Server:
For minor changes that don’t necessitate a complete restart, you can reload the Apache web server:
sudo systemctl reload apache2Disabling Apache on Server Boot:
sudo systemctl disable apache2Enabling Apache on Server Boot:
This is typically enabled by default upon installation:
sudo systemctl enable apache2Additional Apache Commands on Debian 12, 11 or 10
As we delve deeper into managing our Apache web server on Debian, it’s crucial to understand some additional commands. This includes updating, upgrading, and even removing Apache when required. These commands can provide a way to ensure optimal performance and security for your server.
Update Apache on Debian
Before initiating the update process, you must check for available updates for your system. This can be done using the apt update command, which fetches information about available updates from the repositories:
sudo apt updateIf there are updates available for Apache, they can be applied using the apt upgrade command. This command will upgrade all installed packages, including Apache, to their latest versions:
sudo apt upgradeA point to consider: creating backups or server images is always wise if your Apache service supports mission-critical applications. Although most updates are safe, occasional unforeseen issues may arise during the upgrade process.
Remove Apache on Debian
To uninstall Apache from your system, the apt remove command can be used. This command not only uninstalls Apache but also removes any unused dependencies that were installed alongside it:
sudo apt remove apache2Final Thoughts
This guide delved into the various aspects of managing an Apache web server on a Debian system. We covered many topics, from initial setup, securing the server with SSL certificates, and managing logs to handling updates and removals. This comprehensive guide is designed to equip you, novice or expert, with the fundamental knowledge necessary to operate Apache effectively. The command line skills gained here apply to Apache and are transferable, enriching your overall experience with the Debian Linux distribution.