This guide will demonstrate how to install SSH on Ubuntu 24.04, 22.04, or 20.04 LTS utilizing the command-line terminal.
Secure Shell (SSH) is a vital protocol for secure communication over unsecured networks. It provides a secure channel for administrators and users to access servers remotely, ensuring that data is encrypted and protected from potential eavesdropping. Understanding the core features of SSH can enhance your network management and security practices. Here’s a snapshot of what makes SSH indispensable:
- Encryption: SSH encrypts all data transmitted between the client and server, safeguarding against eavesdropping and interception.
- Authentication: It supports various authentication methods, including password, public key, and host-based authentication, enhancing security measures.
- Port Forwarding: Allows for the secure tunneling of network connections and can be used to secure other protocols.
- Interoperability: Compatible with a wide range of devices and operating systems, making it a versatile tool for network administration.
- Data Integrity: SSH ensures that the data sent and received remains unaltered, maintaining its integrity throughout transmission.
- Command Execution: Users can securely execute commands on remote machines, aiding in efficient remote management.
- File Transfer: SSH provides secure channels for file transfer, such as SFTP and SCP, ensuring that data remains secure during transit.
- Customization: Offers configuration and customization options to meet specific security policies and requirements.
As we delve into the specifics of installing SSH on Ubuntu, it’s crucial to grasp these features to maximize the benefits of this popular protocol.
Install SSH on Ubuntu via APT
Update Ubuntu Before SSH Installation
Before installing SSH, updating your Ubuntu system’s package list and upgrading the existing packages is crucial. This step ensures that your system is up-to-date and prevents potential conflicts during the installation.
Execute the following command in the terminal:
sudo apt update && sudo apt upgradeThis command first updates the list of available packages and then upgrades the installed packages to their latest versions.
Install OpenSSH via APT Command
After updating your system, proceed to install the OpenSSH server and client. OpenSSH is a suite of secure networking utilities based on the Secure Shell (SSH) protocol, which provides a secure channel over an unsecured network in a client-server architecture.
Use this command to install both the OpenSSH server and client:
sudo apt install openssh-server openssh-clientThe openssh-server component allows your Ubuntu machine to accept SSH connections, while the openssh-client enables it to initiate SSH connections to other machines.
Verify OpenSSH Installation
Post-installation, it’s a good practice to check the version of the OpenSSH server to ensure it’s correctly installed. The following command outputs the version of the OpenSSH server installed on your system:
ssh -VRunning this command, you can confirm that the OpenSSH server is successfully installed and ready to use on your Ubuntu system.
Configure SSH on Ubuntu After Installation
Adjust SSH Configuration Settings
Once OpenSSH is installed on your Ubuntu system, it’s essential to configure it according to your requirements. While the default settings are generally robust, you might need to edit the /etc/ssh/sshd_config file for specific adjustments. This step is crucial for tailoring SSH settings to enhance the security and functionality of your server.
Use the following command to edit the SSH configuration file:
sudo nano /etc/ssh/sshd_configYou can alter various settings within this file to fit your security and operational needs.
Change OpenSSH Ports
Modifying the default OpenSSH port is a strategic security measure to deter unauthorized access attempts. In addition to changing the port, consider implementing restrictions on login attempts and disabling root login to bolster security.
To alter the OpenSSH port, locate the Port line in the sshd_config file and set it to your preferred port number like so:
Port 2222After updating the port number, restart the OpenSSH service to apply your changes:
sudo systemctl restart sshdLimit Login Attempts with SSH
Limiting login attempts in OpenSSH can significantly reduce the risk of brute-force attacks. Edit the sshd_config file again to set the maximum number of authentication attempts:
sudo nano /etc/ssh/sshd_configFind MaxAuthTries and adjust the setting to limit login attempts, for example:
MaxAuthTries 3Save your changes and restart the OpenSSH service to enforce the new limit:
sudo systemctl restart sshdDisable SSH Root Login
Disabling root login over SSH is a recommended practice to prevent direct access to the root account. Edit the sshd_config file again and set PermitRootLogin to no:
PermitRootLogin noSave your changes and restart the OpenSSH service to implement this security measure:
sudo systemctl restart sshdSecure SSH with UFW Rules
The Uncomplicated Firewall (UFW) offers an intuitive way to manage firewall rules on Ubuntu. Ensuring UFW is enabled and properly configured enhances the security of your SSH service. If UFW is not installed, you can install it using:
sudo apt install ufwAllow incoming connections on your SSH port with UFW:
sudo ufw allow sshIf you’ve changed the default port, adjust the command accordingly:
sudo ufw allow 2222/tcpTo restrict SSH access to a specific IP address, specify the allowed IP while setting the UFW rule:
sudo ufw allow from 203.0.113.0 to any port 22These steps help in securing your SSH service on Ubuntu, ensuring a more robust defense against unauthorized access.
Connecting to a Remote Server via SSH on Ubuntu
Establishing a Connection through SSH
Below are steps on how to connect using different authentication methods and ports.
ssh username@remote_serverReplace “username” with your account’s username and “remote_server” with the hostname or IP address of the desired server. When you initiate the command, the system will prompt you for your password to authenticate and successfully establish the connection.
Connecting with Public Key Authentication
For a heightened level of security, SSH supports connections using public key authentication. This method eschews the traditional password input, requiring a private key to verify your identity. To use public key authentication, execute:
ssh -i /path/to/private_key username@remote_serverIn this command structure, /path/to/private_key should be replaced with the actual path to your private key file, while username and remote_server need to be substituted with your user name and the remote server’s IP address or hostname, respectively.
Specifying a Connection Port
SSH traditionally uses port 22 for connections, though some servers may use different ports. To connect through an alternative port, input:
ssh -p PORT_NUMBER username@remote_serverEnsure to replace PORT_NUMBER with the actual port number on which the remote server is listening for incoming SSH connections.
scp /path/to/local/file username@remote_server:/path/to/remote/directory
This command requires modification to reflect the actual file and directory paths on your local system and the remote server, as well as the correct username and remote_server.
Additional Common SSH Commands
For day-to-day operations, you might find the following SSH commands handy:
To copy a directory and its contents to the remote server:
scp -r /path/to/local/directory username@remote_server:/path/to/remote/directoryRun a command on a remote server:
ssh username@remote_server 'command_to_run'
Troubleshoot SSH on Ubuntu
If you encounter any issues with OpenSSH on your Ubuntu machine, here are some standard troubleshooting steps:
Check the OpenSSH logs for any error messages by running the following command:
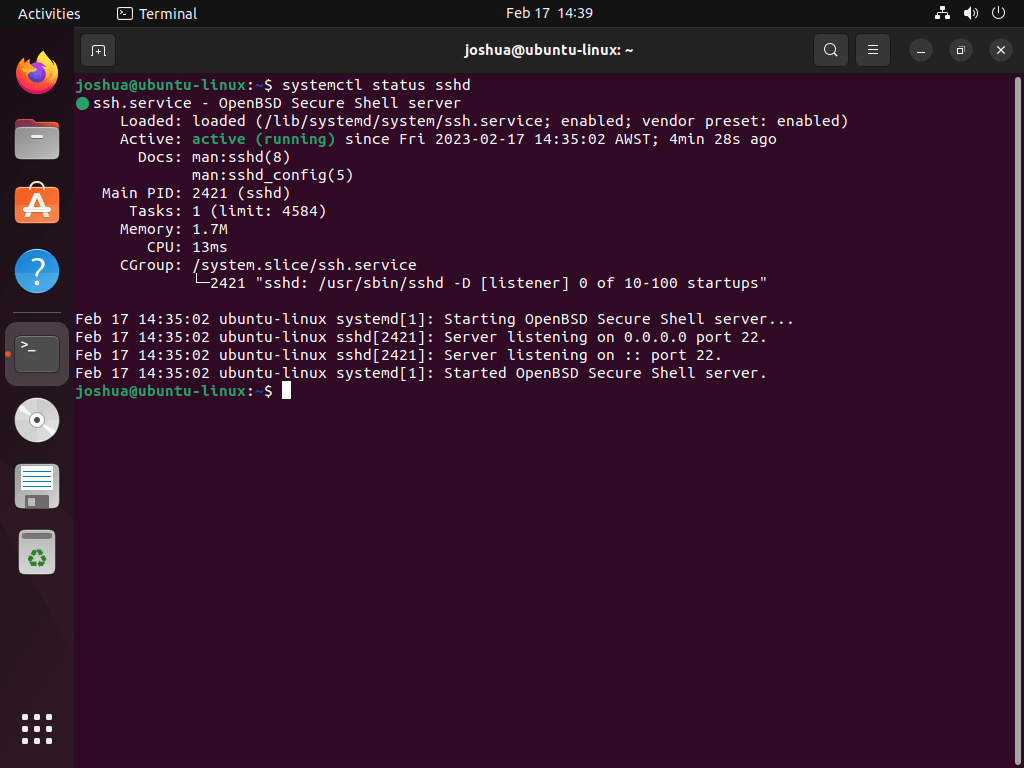
sudo tail -f /var/log/auth.logCheck the status of the OpenSSH service by running the following command:
sudo systemctl status sshd
When reviewing, check for common errors, such as incorrect firewall configuration blocking incoming OpenSSH port connections. Also, ensure the OpenSSH service user has the correct permissions and access to the service.
Conclusion
There you have it! We’ve walked through the steps to install and configure OpenSSH on Ubuntu, ensuring your system’s security with customized settings and UFW rules. Remember, keeping your SSH service secure is an ongoing task, so regularly check for updates and tweak your configurations as needed.
Relevant Links
Explore the following external resources for additional information related to the OpenSSH package on Ubuntu.
- OpenSSH Official Website: Access comprehensive details about OpenSSH, its features, and the latest updates.
- OpenSSH on GitHub: Visit the OpenSSH repository for source code, development updates, and contribution opportunities.
- OpenSSH Manual: Dive into the official manual for in-depth documentation and usage guidelines of OpenSSH.
- OpenSSH on Ubuntu: Learn about managing and configuring OpenSSH specifically on Ubuntu systems.