AppArmor, short for Application Armor, is a Linux Security Module (LSM) that provides a set of tools to protect your system at the application level. It’s a powerful security framework that restricts programs’ capabilities with per-program profiles. These profiles can allow or deny access to specific files, directories, network connections, and other resources.
Why Should Linux Mint Users Learn About AppArmor?
As a Linux Mint user, understanding AppArmor is crucial for several reasons:
- Enhanced Security: AppArmor provides an additional layer of security to your system. It confines programs to a limited set of resources, preventing them from accessing unauthorized files or services.
- Granular Control: With AppArmor, you can define policies for individual applications, giving you granular control over your system’s security.
- Ease of Use: Unlike some other security modules, AppArmor is relatively easy to manage and configure. Its profiles are straightforward to understand and modify, making it accessible even to less experienced users.
- Default in Many Distributions: AppArmor is the default LSM in several popular Linux distributions, including Ubuntu and its derivatives like Linux Mint. Therefore, knowing how to manage it is a valuable skill for any Linux user.
Why Would You Want to Disable or Enable AppArmor?
There might be situations where you need to disable or enable AppArmor:
- Troubleshooting: If you’re experiencing issues with a specific application, you might need to disable AppArmor temporarily to determine whether it’s causing the problem.
- Performance: While AppArmor’s impact on system performance is generally minimal, in some specific scenarios, disabling it might slightly improve system performance.
- Testing New Applications: If you’re testing a new application or developing your own, you might need to disable AppArmor to avoid any unnecessary restrictions.
- Enhancing Security: On the other hand, if you’ve previously disabled AppArmor, you might want to enable it again to take advantage of its security features.
To summarize, AppArmor is a powerful tool that can significantly enhance your system’s security. However, like any tool, it’s essential to understand how to use it properly. Whether you’re troubleshooting an issue, testing a new application, or simply looking to improve your system’s security, knowing how to enable or disable AppArmor can be incredibly useful.
The guide will demonstrate how to enable or disable AppArmor service on Linux Mint 21 or Linux Mint 20.
Step 1: Install the Required Packages
To utilize the full range of AppArmor functionality, it’s important to have the “apparmor-utils” package installed. Some of the commands discussed in this guide may not be available without this package. To install the package, open your terminal and run the following command:
sudo apt install apparmor-utils apparmor-notify apparmor-profiles apparmor-profiles-extra
Step 2: Check AppArmor Status
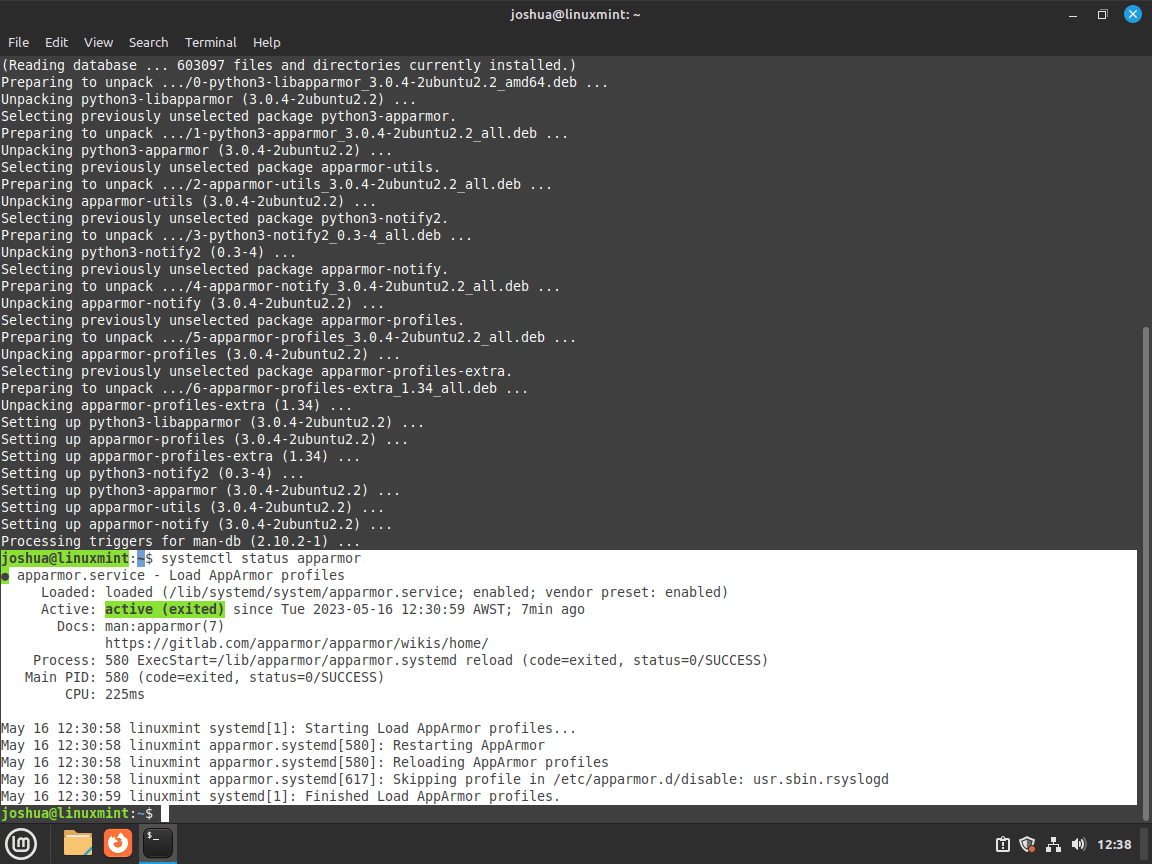
By default, AppArmor is installed and turned on when installing Linux Mint. To verify its status, use the following command:
systemctl status apparmorExample output:
This command verifies that AppArmor is working with systemd, which is an important first step. While there are other methods for checking the status of AppArmor, using the above command as a starting point is a good practice.
Here are some additional systemd commands you might find useful:
- Stop AppArmor:
sudo systemctl stop apparmor- Disable AppArmor on system boot:
sudo systemctl disable apparmor- Start AppArmor:
sudo systemctl start apparmor- Enable AppArmor on system boot (default):
sudo systemctl enable apparmor- Restart AppArmor:
sudo systemctl restart apparmor- Reload AppArmor:
sudo systemctl reload apparmorStep 3: Check AppArmor Profiles Loaded
Before making any changes to AppArmor, it’s crucial to check the status of its profiles. This can be accomplished by using the following command:
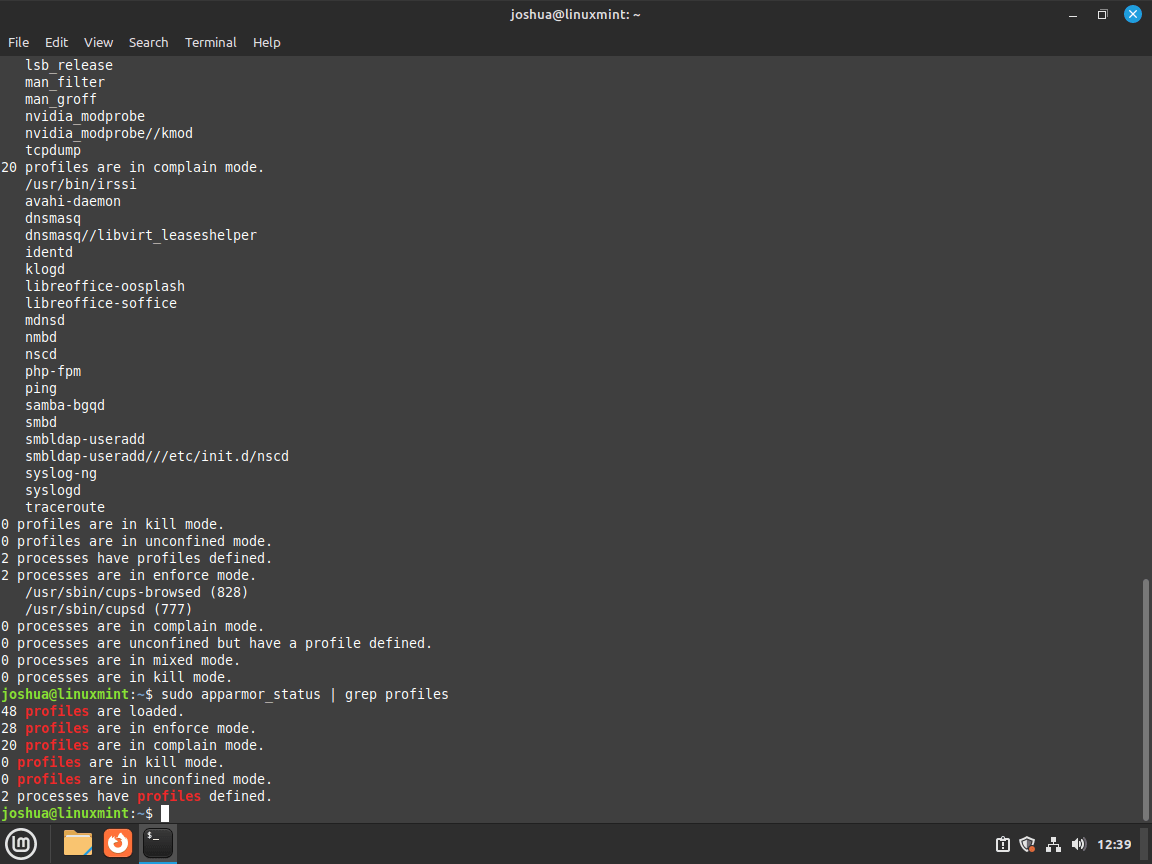
sudo apparmor_statusOr to filter to profiles loaded:
sudo apparmor_status | grep profilesExample output:
This command will provide you with the current status of AppArmor on your system, including which profiles are loaded, the mode in which they are running, and the number
of processes associated with each profile. This information is essential for making informed decisions about enabling or disabling AppArmor on your Linux Mint system.
Another option for checking the status of AppArmor profiles is to use the aa-status command. This command will give you a more detailed and exact readout of the current status of AppArmor on your system.
sudo aa-statusBefore making any changes, it’s also recommended to back up your AppArmor profiles. This can be done with the following command:
sudo cp -R /etc/apparmor.d /etc/apparmor.d.bakThis will create a backup of your AppArmor profiles in the /etc/apparmor.d.bak directory, so you can quickly revert to them in case of any issues. With this backup in place, you can safely proceed with enabling or disabling AppArmor on your Linux Mint system.
Step 4: Disable AppArmor Profile
If you need to disable a specific AppArmor profile, you can do so without disabling the entire security application. This is useful if a particular profile is causing issues on your system, but you still want to keep AppArmor enabled for other profiles.
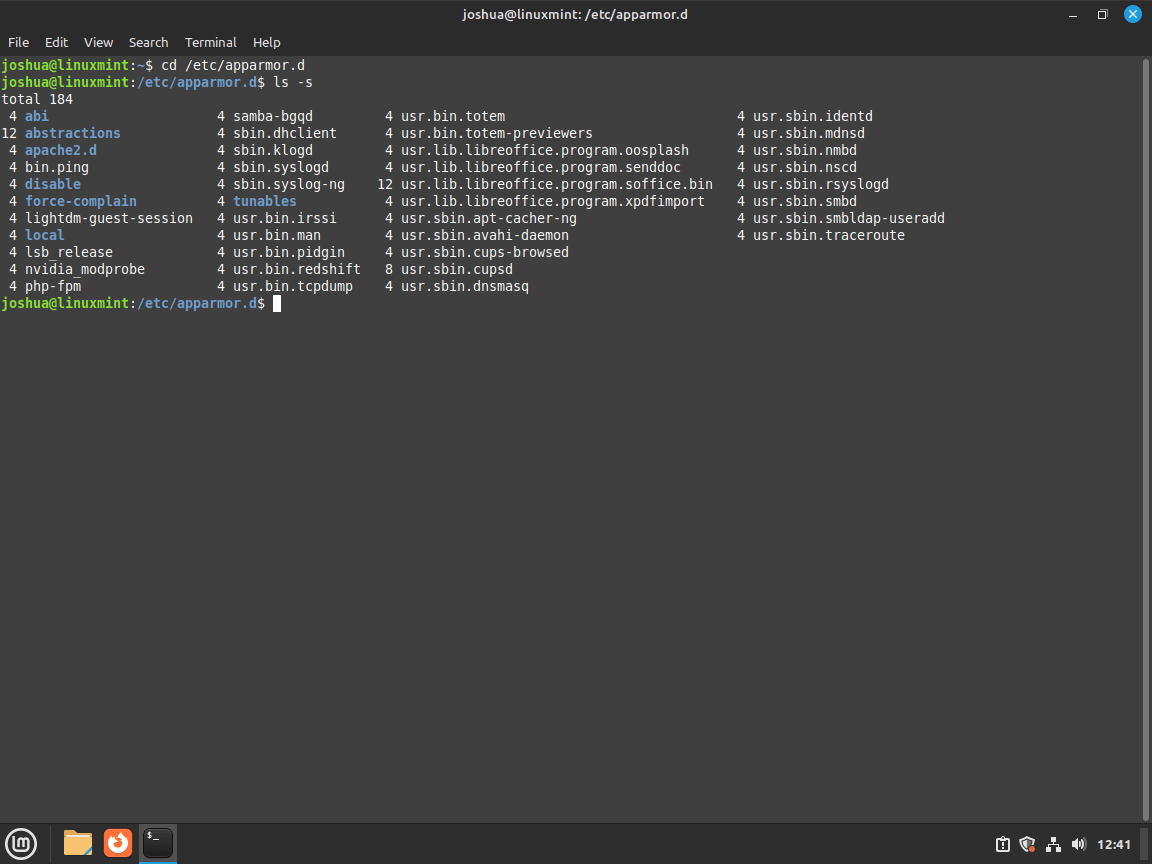
First, navigate to the /etc/apparmor.d directory:
cd /etc/apparmor.dNow, use the ls command to list the profiles in the /etc/apparmor.d directory:
ls -sExample output:
To disable a profile, you would use the following command:
sudo aa-disable /etc/apparmor.d/<profile-name>For example, to disable the usr.sbin.cupsd profile, you can use the following command:
sudo aa-disable /etc/apparmor.d/usr.sbin.cupsdThis will effectively disable the usr.sbin.cupsd profile, and the changes will take effect immediately. To view a list of the rules that are currently disabled, you can navigate to the /etc/apparmor.d/disable directory and use the ls command:
ls /etc/apparmor.d/disableStep 5: Enable AppArmor Profile
To re-enable a profile that has been disabled, you can use the following command:
sudo aa-enable /etc/apparmor.d/<profile-name>For example, to re-enable the usr.sbin.cupsd profile, you can use the following command:
sudo aa-enable /etc/apparmor.d/usr.sbin.cupsdFurther Learning with AppArmor Commands
After you have learned some of the basic commands of using AppArmor to disable or enable profiles and check their status, let’s go over some of the most commonly used AppArmor commands and their usage.
- Using the
aa-genprofCommand
The aa-genprof command generates a new AppArmor profile based on the current system activity. It logs all the application’s system calls and creates a new profile based on this log data. This is useful for creating profiles for new applications that do not yet have a profile defined.
Example: To generate a new profile for the application “firefox,” run the following command:
sudo aa-genprof firefox- Using the
aa-enforceCommand
The aa-enforce command enforces the AppArmor profiles on a Linux Mint system. This command is handy when you have changed your AppArmor profiles and want to immediately enforce the new policies without restarting the system.
Example: To enforce the current AppArmor profiles, run the following command:
sudo aa-enforce /etc/apparmor.d/*Or enforce the profile individually:
sudo aa-enforce /etc/apparmor.d/<profile-name>- Using the
aa-disablecommand
The aa-disable command is used to disable a specific AppArmor profile. When a profile is disabled, the restrictions and permissions that it imposes on the application it governs are no longer in effect. This can be useful if a profile is causing issues or if you need to allow the application more freedom temporarily.
To use the aa-disable command, pass it the name of the profile you want to disable. For example, you would run the following command to disable the profile for “Firefox”:
sudo aa-disable /etc/apparmor.d/firefoxIt’s worth noting that disabling a profile is a temporary change, and the profile will be re-enabled if you reboot your system or restart the AppArmor service.
- Using the
aa-complainCommand
The aa-complain command switches a profile to “complain mode.” AppArmor will still enforce the profile in this mode, but instead of denying access to restricted resources, it will log a message to the syslog. This can be useful for testing and debugging purposes, as it allows you to see what kind of access a profile would be blocking without actually blocking it.
Here’s an example of how to use the aa-complain command:
sudo aa-complain /etc/apparmor.d/usr.sbin.cupsdIn this example, the aa-complain command is being used to switch the usr.sbin.cupsd profile to complain mode. Note that you will need to replace usr.sbin.cupsd with the name of the profile you wish to switch to complain mode.
- Using the
aa-remove-unknowncommand
The aa-remove-unknown command removes AppArmor profiles for unknown applications on a Linux Mint system. This command is useful when you want to clean up your AppArmor profile collection and remove any profiles that are no longer in use.
Here is an example of using the aa-remove-unknown command:
sudo aa-remove-unknownThe aa-remove-unknown command helps clean up your AppArmor profile collection on a Linux Mint system. Using this command, you can easily remove profiles for unknown applications, keeping your profile collection organized and up-to-date.
These are just a few examples of what you can accomplish with AppArmor commands. There is much more available to explore.
Closing Thoughts on Enabling or Disabling Apparmor
In conclusion, enabling or disabling AppArmor profiles on Linux Mint is simple and straightforward. By following the steps outlined in this guide, you can easily manage the security of your system and control which applications or services are protected by AppArmor. Whether you need to temporarily disable a profile for maintenance or troubleshooting or permanently remove protection for an application, the commands and tools discussed in this guide will help you achieve your goals.
Additional Resources and Links
- Official AppArmor Documentation: The official AppArmor documentation is a comprehensive resource that covers all aspects of AppArmor, from basic usage to advanced configuration. It’s a must-read for anyone serious about mastering AppArmor. Visit Official AppArmor Documentation
- Linux Mint Community: The Linux Mint Community is a great place to connect with other Linux Mint users, ask questions, and share your experiences. Visit Linux Mint Community
- Ubuntu AppArmor Wiki: Although this guide is for Linux Mint, the Ubuntu AppArmor Wiki is a valuable resource as Linux Mint is based on Ubuntu. The wiki provides a wealth of information about AppArmor’s usage and configuration. Visit Ubuntu AppArmor Wiki
- Stack Overflow: Stack Overflow has a vast number of questions and answers related to AppArmor. It’s a great place to find solutions to common problems and learn from the experiences of other users. Visit Stack Overflow
- Linux Security Module (LSM): AppArmor is a type of Linux Security Module (LSM). To understand more about how LSMs work and how they contribute to system security, check out the LSM documentation on the kernel.org website. Visit Linux Security Module (LSM)